October Consumer Cyber Safety Pulse Report


Do you have internet trust issues? If so, you probably take steps to avoid anything suspicious when you go online. But what about those online activities you already trust?
New research from Norton Labs uncovered three unexpected ways your privacy and security could be put at risk — and all in time for the holiday season.
Learn more in this issue of the Consumer Cyber Safety Pulse Report.
- Spotlight #1: Weak two-factor authentication. That code on your smartphone might not keep you safe when logging into your accounts.
- Spotlight #2: E-Commerce scams. Reports of online shopping fraud doubled since 2019, and they’re ready for a 2022 holiday boom.
- Spotlight #3: Leaky websites. Trying to sidestep nosy search engines? Eight of 10 websites will still peddle your search info.
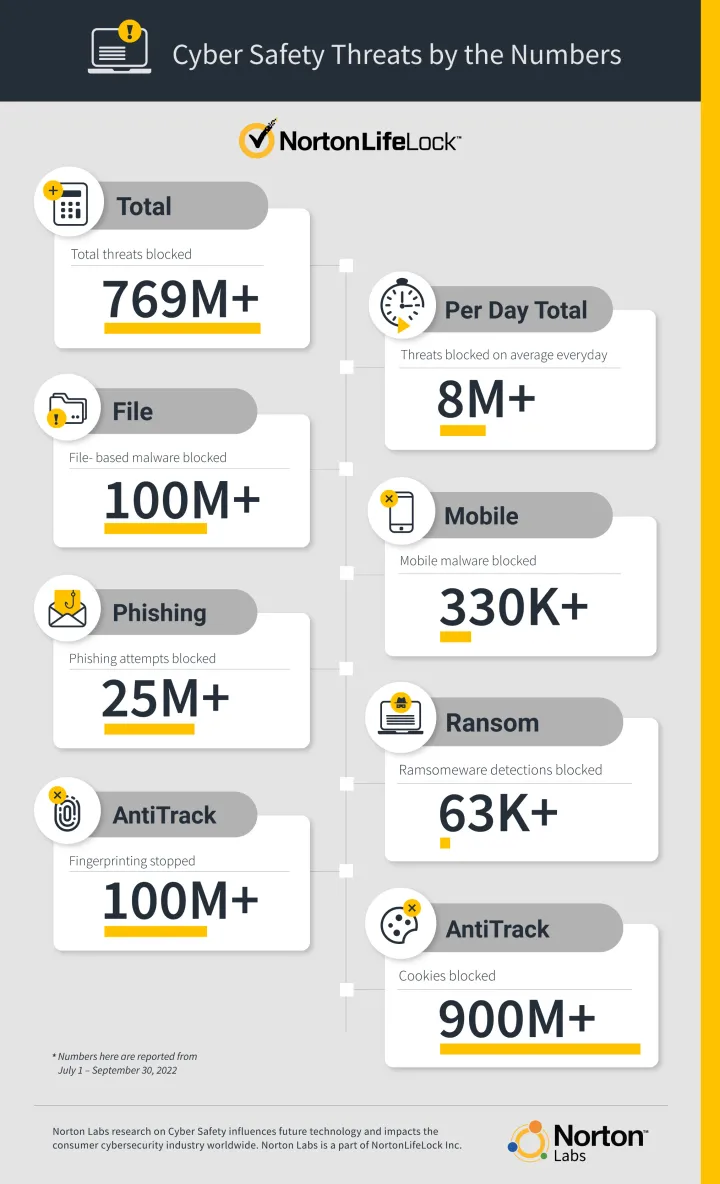
But first, here's a look at the numbers. We've included some new stats about Norton AntiTrack, which blocked more than 1 billion trackers and fingerprinting scripts last quarter to help keep our user’s personal information and browsing activity private.
Spotlight #1 – Weak two-factor authentication puts us all at risk, and companies know it
Background: Recently several important companies were compromised via stolen login credentials. For most of them, their two-factor authentication (2FA) systems were defeated. Some of these companies provide critical services that are fundamental to how we use the internet. These targeted attack campaigns sought to not only steal information that could later be monetized, but they also to undermine the trusted technologies used to send automated emails, one-time authentication codes sent via SMS, entire company’s single sign-on, and the availability of millions of websites.
Cybercriminals have already become very good at catching the one-time codes used in most types of two-factor authentication. They also know that undermining the systems that send or generate the one-time codes makes their efforts even more effective. Not only do these attacks reveal the shortcomings of the most widely used types of 2FA, but they also illustrate just how large the blast radius could have been if these ongoing attacks were more successful.
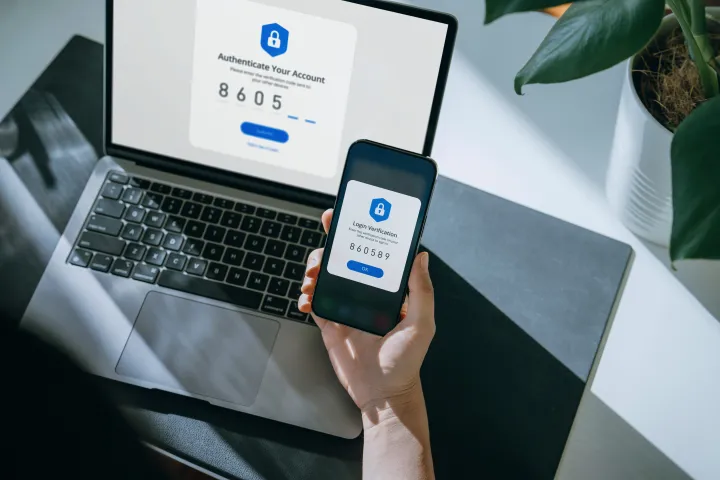
Bottom line: While the one-time authentication codes used in most types of two-factor authentication are better than nothing, they are only barely so. Expert Roger Grimes literally wrote the book on hacking 2FA and has extensively covered the use of use weak, phishable 2FA. The U.S government began prohibiting weak 2FA in 2017 and continues to educate on the risks of weak 2FA. With all this in mind, companies need to begin supporting hardware tokens to defend against these attacks.
Advice for Consumers: Wherever possible, use Fast IDentity Online universal two-factor (FIDO U2F) authentication. FIDO U2F is a standard for physical hardware tokens that work with devices and isn’t susceptible to the types of phishing attacks people encounter. You can buy these tokens from Yubico or Google and use them with all the companies that support them. You can also request companies that don’t support FIDO U2F tokens begin doing so through customer service requests. Remember: these companies know their phishable 2FA is inadequate.
Spotlight #2 – E-Commerce Scams
Background: Many entrepreneurs find that running an e-shop, in conjunction with a social media presence, is a great way to build a community where they can offer great products to customers around the world. This became even more important during the COVID-19 pandemic, as many people began to increase how much they shopped online. With this increase in online shopping came an increase in scammers trying to defraud shoppers. According to the FTC, in 2019 there were 180,822 reports of online shopping fraud. By 2021 that number jumped to 397,826 and totaled $392 million dollars in losses.
How it works: New scam e-shops are appearing every day, offering anything they think someone would be interested in buying; electronics, jewelry, clothes, animals, medical equipment, crystals, etc.
These sites use all the tricks in the book to seem legitimate - engaging domain names, polished storefronts, photoshopped images, glowing reviews and customer stories, plenty of payment options, ties to social media accounts, and much more.
However, when you place an order there is no telling what will happen next. You may receive some low-quality counterfeit item that is similar (yet different) to the item advertised in the store, or you may receive nothing at all. The only thing you are guaranteed to get is angry.
Advice for Consumers: Knowing what to watch out for can help lower your chances of being scammed by a fake e-shop, but even the most diligent consumer can fall victim to the right scam at the right time. Here are some things to keep in mind when shopping online.
Check the domain. Use a URL lookup tool like safeweb.norton.com to see if it’s already known to be a malicious/scam domain.
Beware of social media and unsolicited messages. The e-shop must get you to visit to be effective, and social media is one way scammers can target people with certain interests to get an ad for the e-shop to cross their paths. Texts and emails offering big sales are another thing to be wary of.
Watch out for prices that are too good to be true. If the price is too good to be true it’s either stolen or fake, either way you probably don’t want to give that website your credit card info and address.
Be wary of any site that pushes you toward unusual payment-processing methods. Many scam sites will offer a wide variety of payment options when you are adding to the cart, but only have one option when it comes time to check out.
Fake e-shops can be very convincing. Never trust your instinct that a site “doesn’t look like a scam.” Phishing and scams have become increasingly convincing over time.
Check the refund policy and about us pages for red flags. Scammers put a lot of effort into the home page, product views, and payment processing, but they often put little effort into the “About Us” and “Refund Policy” pages. These can be red flags.
Many scams try to trick customers with fake reviews. Five-star reviews (especially on a website they are operating) could be fake. Even on public markets like Amazon and Google Play, reviews can be bought.
Spotlight #3 – Search term privacy
More than 80% of the top websites leak user searches to advertisers
Background: While it is more widely known Google uses your search terms to target ads, you may think you can find more privacy with your search terms by searching on websites directly. But our recent study found that more than 80% of websites share search terms with advertisers either accidentally or deliberately.
How it works: Modern websites load a variety of code from other places in the background when you visit a web page — often 30 or more third-party scripts. These trackers can gain certain information from your visit to the website, such as your IP address, the website’s content and domain, and often what you type and even your screen size and device type. These scripts may submit that information back to their origin server. Even just loading these scripts can give the server information, since sensitive information is often contained in what are known as HTTP Request Headers.
Bottom line: These types of leaks may not seem like a big deal, but searches often contain our most sensitive information. We may write about our medical concerns, sexual preferences, family and legal situations — and we would not want or expect those searches to be shared with any third parties. Advertisers may then use these sensitive characteristics to target ads in unexpected or uncomfortable ways.
Advice for Consumers: Ad-blocking and tracker-blocking programs can help mitigate these types of privacy threats by preventing the loading of many third-party advertising scripts in the first place. Norton AntiTrack is one such product.
Looking ahead
Norton Labs continues to track scams and threats targeting the digital lives of consumers. Stay tuned for more cybersecurity intel when we publish our next Consumer Cyber Safety Pulse Report in January.
Editorial note: Our articles provide educational information for you. NortonLifeLock offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about cyber safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses.
Copyright © 2022 NortonLifeLock Inc. All rights reserved. NortonLifeLock, the NortonLifeLock Logo, the Checkmark Logo, Norton, LifeLock, and the LockMan Logo are trademarks or registered trademarks of NortonLifeLock Inc. or its affiliates in the United States and other countries. Other names may be trademarks of their respective owners.