New study finds 8 unique social media phishing lures


Are you active on social media? You could be a target for social media phishing attacks designed to steal your private information.
That’s one of the findings of a new study by Norton Labs. The Labs team analyzed a full year of phishing attacks against social media websites, including Facebook, Instagram, TikTok, Twitter, LinkedIn, and Snapchat.
Among the study’s key findings:
- Phishing campaigns targeting social media use diverse stories to trick a user.
- Social media attacks have become more sophisticated, aided by tools that make campaigns more convincing and easier to unleash.
Here are the top eight social media phishing attacks Norton Labs found in the study:
- Classic login phishing
- Locked accounts notices
- Copyright violation notices
- Verified badge scams
- Profile hacking services
- Follower generator services
- Two-Factor authentication interception
- Payment fraud
We take a closer look at each lure with examples below, but first, here is a look at what’s driving the attacks.
Why do scammers target social media?
Social media connects people around the world. Platforms like Facebook, Instagram, TikTok, Twitter, LinkedIn, and Snapchat are often used to interact with friends and colleagues. They’re also used as a tool for accessing news, purchasing products, finding a job, watching videos, and much more.
More than 4 billion people use social media worldwide, sharing their personal information, where they live, what they like, what they are interested in, and who they interact with. Users’ data provides social media companies with information, which allows advertisers to target specific audiences with marketing they think will be effective on that specific group.
For these same reasons, threat actors like social media too. The platforms have become one of the main targets for phishing attacks in recent years and represent a low-effort way to target billions of people anywhere in the world.
The phishing lure list: Watch out for these eight social media phishing tricks
Here’s a closer look at the eight lures we detected, with real-world examples and context. These are all phishing pages; none is from the official company that they are pretending to be.
1. Classic login phishing
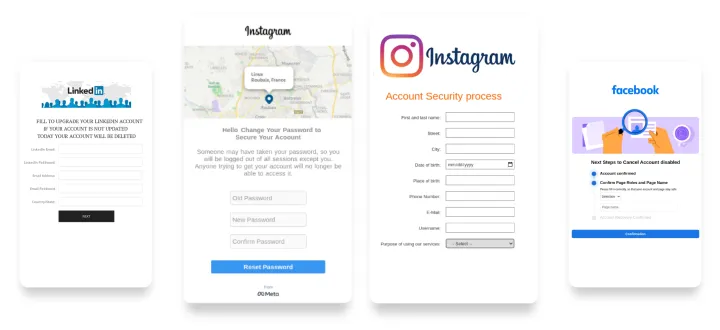
The creation of a website that is similar in name and appearance to the official social-media login page represents the most common and widespread phishing scheme. This template is used to fool users into believing that the page is legitimate, and to steal their credentials once they try to access their profile.
2. Locked accounts notices
This phish exploits users’ fear of losing access to the account to steal their credentials. Phishing websites of this kind usually scare consumers to reveal sensitive information by reporting a fake unauthorized new login to their account, the presence of outdated information that must be updated, or the need to go through a security checklist to keep an account secure.
3. Copyright violation notices
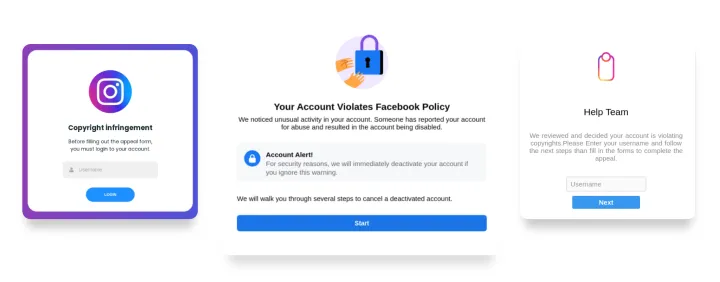
Social platforms are not authorized to post material without permission from the copyright holder and have stringent rules to restrict its users from posting a third party’s copyrighted material. Such a clause is leveraged in phishing attacks to deceive users and pretend that the victim’s account has been locked because they violated copyright rules. With this kind of malicious website, victims are required to log in and disclose their credentials to unlock their profiles.
4. Verified badge scams
Verified badges are icons that appear on some social media sites to indicate that the platform has confirmed that an account is the authentic presence of the public/popular figure, celebrity, or brand it represents. Generally, accounts that have been verified are more trusted and may get other advantages like a broader reach for their content. Phishing campaigns use the promise of getting a verified badge to lure users into providing login details to the target site. Malicious pages present users with a prompt that asks users to login to obtain, or not to lose, their verified status on the platform.

5. Profile hacking services
Profile hacking services represent a recent variant of phishing attacks targeting social media. Malicious campaigns based on hacking services often pretend to offer users a way to hack into a profile or to reveal other customers’ information such as email addresses or their list of interactions. In most cases the goal of these campaigns is not to steal credentials, but to continuously redirect victims and monetize from other services such as ads or surveys.

6. Follower generator services
Generating followers and interactions is one of the main goals of some users who want reach and influence. This is not an easy task, and some people want to take short cuts like paying for followers and other types of engagement. This desire is leveraged by another phishing scheme that promotes services to do that at a low or no cost at all. Such attacks can yield profit by redirecting victims to some attacker-controlled websites that display ads, can lure users to reveal login credentials, or can facilitate the spread of malicious software that victims are required to install .

7. Two-Factor authentication interception
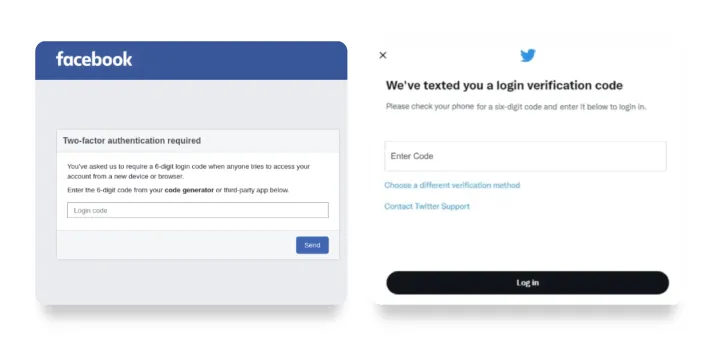
While many users are already familiar with two-factor authentication, it might surprise them to learn that their two-factor authentication codes from an app or SMS can also be captured via phishing. For those already familiar with logging in with a two-factor code, a phishing site prompting them for a code just follows a learned log-in behavior.
Sneaky phishing campaigns aim instead to intercept temporary codes to break into profiles with two-factor authentication enabled. Those tokens are generally tied to the victim’s phone number or a code generator app on their device and are typically required to login and make changes to an account
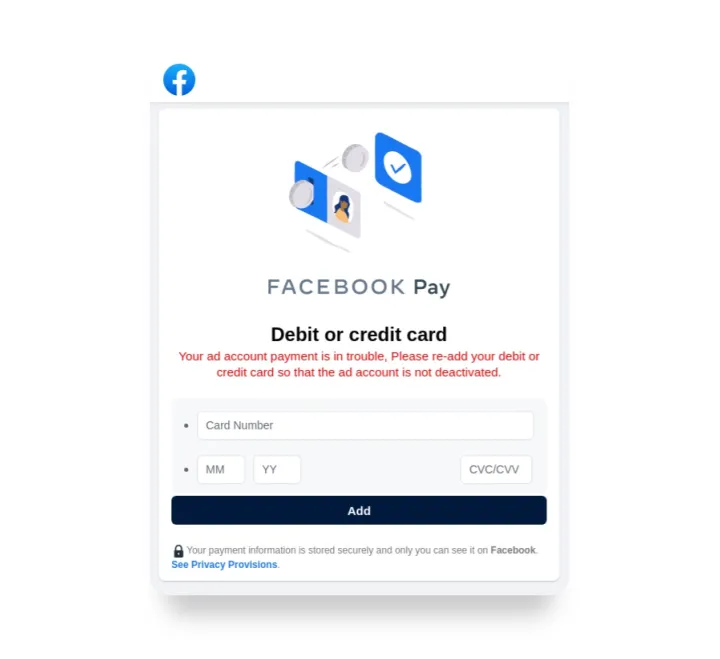
8. Payment fraud
Threat actors also design phishing campaigns that aim to steal financial information from the users. Malicious websites usually exploit known social media brands and ask for credit card details from their victims by simulating a problem with their account.
Wrap-up
The reason these lures matter is because they have an impact beyond revealing your login information for one company or service. They can take a financial toll on the victim or their contacts, are used to further spread the phishing campaign, and much more. According to the FTC, consumers reported $770 million in losses related to fraud that started on social media in 2021. While not all of that is related to phishing scams, it highlights why scammers are trying so hard to get people to reveal their login details, and why you should be on the lookout for these scams as well as whatever they come up with next.
Editorial note: Our articles provide educational information for you. NortonLifeLock offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about cyber safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses.
Copyright © 2022 NortonLifeLock Inc. All rights reserved. NortonLifeLock, the NortonLifeLock Logo, the Checkmark Logo, Norton, LifeLock, and the LockMan Logo are trademarks or registered trademarks of NortonLifeLock Inc. or its affiliates in the United States and other countries. Other names may be trademarks of their respective owners.