Over-The-Air Updates Raise Risks For Android Users
An analysis of firmware update apps on Android finds PUPs and malware
System updates are an important part of your Cyber Safety. But within the Android operating system, updates can also create security risks for Android users, including installing malware. Here’s how it happens.
Android is the most-used operating system ever, with more than 2.5 billion active Android devices. Part of Android’s success is due to the openness of the platform, which allows any device manufacturer to customize and deploy their own Android version.
Paradoxically, this open model has resulted in a poorly understood ecosystem of actors that play key roles at different stages of the Android supply chain. Platform updates are a particularly critical and highly privileged element of the Android ecosystem. Once a patch or a new Android version is released, each vendor needs to ship it over-the-air to their user base.
A Firmware-Over-The-Air (FOTA) app is the software responsible for downloading and applying these updates on the device. Due to the way that system updates are done on Android, FOTA apps need to operate with elevated privileges.
Despite the critical importance of FOTA apps, many aspects of them have been overlooked. A few examples:
- Who is responsible for system updates?
- What are the capabilities of FOTA apps and what information they collect?
- Can FOTA apps jeopardize the security and privacy of a device?
- Are FOTA apps used for secondary purposes beyond system updates?
In a study led by Universidad Carlos III de Madrid, in collaboration with researchers from IMDEA Networks Institute, NortonLifeLock, and the International Computer Science Institute (ICSI), we sought answers to these questions by analyzing 2,013 FOTA apps collected from real world devices.
The results of our study appeared at the 42nd IEEE Symposium on Security and Privacy (S&P) conference in May 2021.
Who can update my phone?
Most users may expect that device vendors are responsible for applying system updates, because they are technically the ones that build the operating system. However, this is only part of the picture.
Only 53% of the 2,013 FOTA apps we analyzed belong to Original Equipment Manufacturer (OEM) vendors. The remaining belong to third party vendors like System on Chip (SoC), Mobile Network Operators (MNO), and Specialized FOTA Developers (SFD).
There are legitimate reasons for these entities to deploy their own FOTA apps. For example, a device vendor may outsource the development or deployment of FOTA apps to SFD vendors. SoC FOTAs may be used for updating specific hardware components while FOTAs from MNO vendors may be present in devices for installing specific updates and system apps, like app centers or commercial apps, that a user cannot remove.
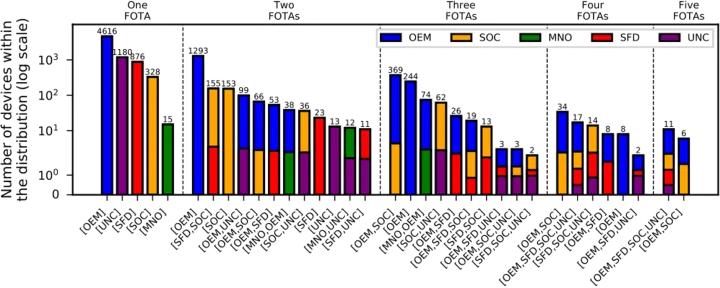
What is interesting is that multiple FOTA apps may coexist on the same device. Although 71% of the devices in our dataset have only one FOTA, the remaining 29% of the devices have two to five FOTAs.
Figure 1 shows the distribution of FOTA types in devices. In general, we observed that for most of the devices with one or two FOTAs, the FOTAs are from OEMs. In absence of an OEM FOTA, it is common to observe either a FOTA from an SFD or SoC. Indeed, often combinations of FOTAs from different categories include one from an SoC.
Our analysis confirms that the Android update ecosystem is fragmented, with updates coming from a variety of actors at any given time. This fragmentation together with the difficulties in FOTA app attribution may affect the transparency of the supply chain and may hinder accountability. In cases where malicious installations are applied, due to the presence of different FOTAs in a device, it is difficult to track which one installed the malicious component.
Security Implications
Due to their critical nature, system updates must be performed in a secure manner. The main protection mechanism relies on the signature verification of the updates. The update file must be signed with the provider’s key, which is checked against the system OTA certificates stored in the otacerts.zip. The owners of the certificates included in the otacerts.zip can install system packages as part of the update process.
However, the lack of control over the FOTA signing process has security implications. We find 40 FOTA apps that are signed with default (thus well-known) test-keys released as part of the Android Open Source Project (AOSP). We discover at least 171 devices from 20 brands (including Alps, Xiaomi, Samsung) with such issues. Apps signed with the same keys can gain system privileges on these devices.
In addition, we found 87 devices in which their otacerts.zip file contains an AOSP default key, thus accepting any update signed with the same key. These devices are mostly from the brand Alps (57%) and Goclever (12%), but we also find devices from brands such as Huawei (3%), Toshiba (3%), and Samsung (1%).
We responsibly disclosed these findings to Google and the main vendors involved.
Privacy risks
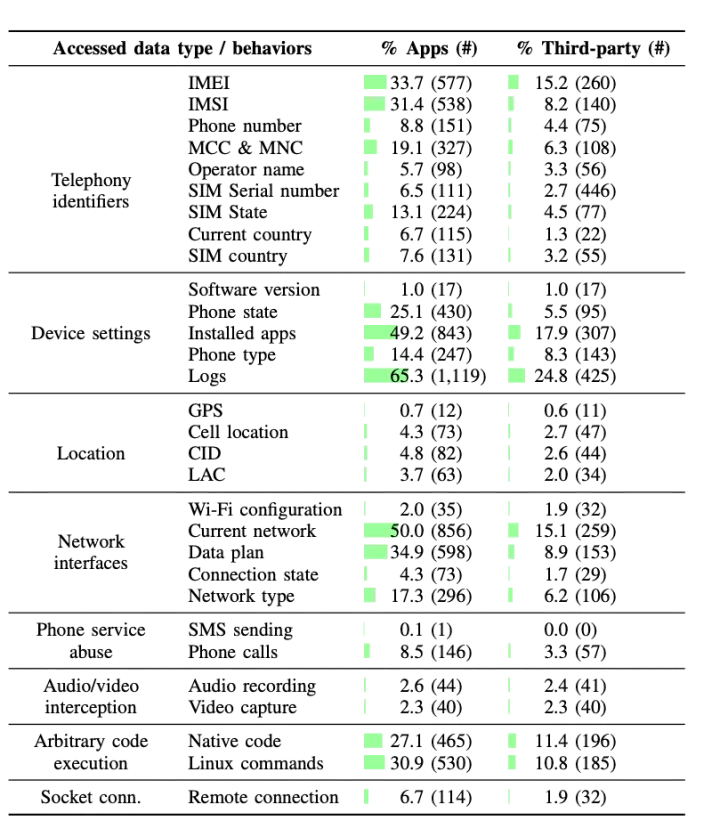
We statically analyzed 1,716 non-Google FOTA apps to characterize their capabilities and identify potential privacy risks. Figure 2 shows a summary of the personal data accessed by FOTA apps.
Most FOTA apps show capabilities that are expected given their function. For example, most apps access the current and network and phone state since Google recommends system updates to occur when the device is in idle maintenance mode and when connected to a Wi-Fi network. However, our findings suggest a prevalent access to various user and device identifiers. The purpose of uploading such identifiers is unknown, although one plausible hypothesis is that they facilitate targeted installations programs. Interestingly, we also observed a small number (<5%) of FOTA apps that access the device location.
An analysis of the third-party components in FOTA apps revealed that 10% of FOTA apps make use of 8 SDKs related to social networks, user tracking, and advertisement. It’s unclear how the presence of these components may facilitate system updates. However, this can become problematic, from a privacy perspective, since FOTA apps are highly privileged and embedded third-party SDKs run with the same permissions.
What FOTA apps install beyond system updates?
We complemented our previous analysis with an analysis of the installation behavior of FOTA apps as observed in the NortonLifeLock telemetry. We are able to detect installation events for 20 FOTA apps. The reason for the low coverage is that the telemetry uses the PackageInstaller for obtaining the installer information, and FOTA apps may install apps via other means (e.g., as an update of the system partition, or through the execution of external programs).
We observed that 13 out of 20 FOTA apps install third-party applications that exist in the Google Play store. These third-party apps belong to various Google Play store app categories but most commonly to Tools, Entertainment, Communication, and Games. This shows that FOTA apps, in addition to system updates, are used for secondary or commercial purposes — possibly for promoting third-party apps.
Because FOTA apps appear to install a variety of non-system packages, we were interested in checking if any of those are malware or Potentially Unwanted Programs (PUP). We discovered seven FOTA apps that install at least one unwanted app (malware or PUP).
These unwanted apps are mostly PUP, but we observed one FOTA app, from Qiku device vendor, installing instances of various malware families, including trojans like triada, necro, and guerilla. These malware installations take place possibly due to compromised third-party vendor code included in the OEM images, such as in the case of the triada trojan that was found in the devices of several OEM vendors.
This is very problematic because unwanted apps installed under the system partitions cannot be removed by users or by security tools, instead requiring an OEM update.
Conclusions
Our work illustrates that the presence of many different stakeholders in the FOTA ecosystem leads to a complex and fragmented ecosystem.
The use of FOTA apps makes the supply chain dynamic during the life cycle of a device, since system apps present in a device could be pre-installed or installed and patched at a later stage as part of an update.
Our static analysis of FOTA apps allowed us to observe potential privacy-intrusive practices, while the telemetry analysis confirmed that FOTA apps install third-party apps beyond system updates, including in some cases, unwanted apps like adware or malware.
Security updates have always been an issue in the Android ecosystem. That’s why Google implemented two new projects aiming at improving the life cycle of security updates — Project Treble and Project Mainline.
Project Treble makes a better separation between AOSP code and vendor-specific components. Project Mainline allows the Google Play store to apply AOSP updates directly in the devices which reduces patching delays.
Although these are steps in the right direction, they do not fully solve the issues discovered in this work, which emerge from the complexities of the supply chain and the many stakeholders involved.
While this is not an easy-to-solve problem, we recommend FOTA developers to follow best practices on FOTA development, provided in the Android official documentation. We also encourage FOTA developers to increase transparency through public documentation.
We find that system updates are commonly implemented by various FOTA apps in the same device, with vague attribution signals. This hurts accountability in case that bad practices are observed, since it makes it hard to know where the updates come from.
Finally, it’s important for FOTA apps to focus only on updating system components, leaving user-level installations to other less privileged apps.
Innovations from Norton Labs are for research, evaluation, and consumer feedback purposes. NortonLifeLock does not give any warranties as to the suitability or usability of these prototypes and recommends safeguarding data and reviewing all terms and conditions before use.
Copyright © 2021 NortonLifeLock Inc. All rights reserved. NortonLifeLock, the NortonLifeLock Logo, the Checkmark Logo, Norton, LifeLock, and the LockMan Logo are trademarks or registered trademarks of NortonLifeLock Inc. or its affiliates in the United States and other countries.







We encourage you to share your thoughts on your favorite social platform.