To Click, or Not to Click, that is the Question: Towards a New Era of Transparency
Poor Click Hygiene Could Increase Risks to End Users
Browsing the web can expose users to important security risks. Through malicious and compromised web pages, computers can become infected with malware that can facilitate the theft of log-in credentials and other personal information from users. Recently, online tracking of your browsing history has become a major privacy concern. Privacy-conscious users must exercise caution when visiting webpages and pay attention to warnings provided by their browsers about potentially dangerous hyperlink destinations.
Web pages have evolved into complex and dynamic applications, which are often opaque and difficult for non-experts to understand. At the same time, security researchers push for more transparency in web applications, which can help users make wiser security-related decisions as far as which information to disclose, which links to visit, and which online services to trust. In a recent study we conducted, soon to be presented at The Web Conference (WWW), we took a closer look at the click ecosystem and discovered that click-related bad practices do not only exist on dubious web sites but also on highly reputable websites.
An Example is Worth a Thousand Definitions
Let us examine some of these bad practices using a concrete example that we came across during our experiments. This way, we can better understand what website owners are doing and what the potential consequences could be for the end users.
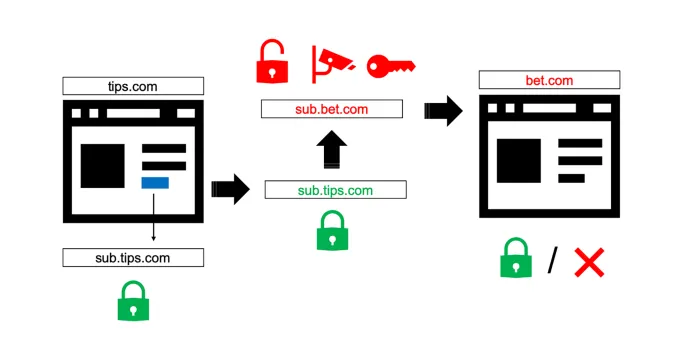
The user browses to a popular website x.com which is offering online betting discounts and tips. When the user clicks on a discount (which points to the same domain x.com), she is redirected to that target first, but is then immediately redirected to an external betting company (y.com), and finally to the promotional discount on y.com. Both the second and third redirections are deceiving, as they result in the user visiting a third-party website without her consent. But the main problem, in this case, is the second redirection. In fact, while the original destination is secure (over HTTPS) and the final website is also served over HTTPS, the intermediate access occurs over an unencrypted HTTP connection. To make matters worse, the intermediate connection is completely invisible to the user. As the original and final websites use HTTPS, a visitor may erroneously believe that the entire chain of redirection was secure, while in reality the user could be subject to a possible man-in-the-middle attack. Moreover, she is also subject to a possible eavesdropper that can read all information sent. While analyzing this example for our case study, we realized that the user can even have her credit card indirectly compromised. Therefore, a malicious actor could later reuse these cookies to access and withdraw money from the account.
Let’s See What Clicks are Currently Doing
Even though the security tip of ‘check the URLs before clicking on them’ has been repeated countless times to users, no one to date has measured to what extent this action is possible or how effective – since some web design choices can make this step impossible for users to perform. While looking closely at this problem, we measured the prevalence of bad practices and whether they are becoming the norm rather than the exception.
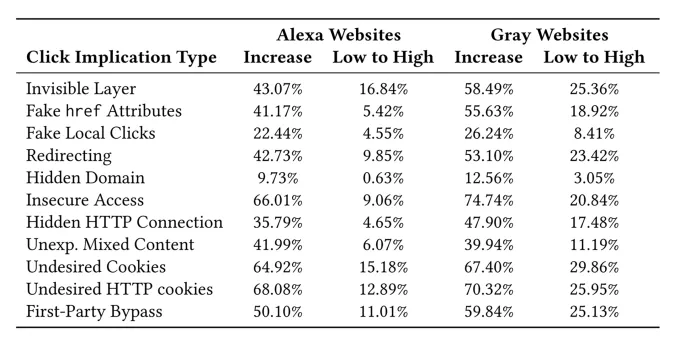
We analyzed around 2.5M different clicks in the wild (in highly accessed and gray websites) and, unfortunately, found that the aforementioned bad practices are not rare. Approximately 80% of the domains adopt some type of misleading technique that would prevent users from making informed decisions about their clicks. Moreover, around 70% of the domains exposed users to unexpected man-in-the-middle threats, 20% of which were completely undetectable by a user even after the click was performed. Even worse, 10-20% of the time a link pointing to a low-risk website resulted in a visit to a site categorized as highly dangerous (see the figure for more concrete data).
Formalizing a Click Contract
Today, there are no clear guidelines that define what should be the acceptable behavior when a user clicks on an element of a web page. However, there exist several important assumptions, which users and web developers often take for granted, that characterize such expected behavior. In order to formalize a click contract, we propose a number of rules that are based on previous web recommendations/standards and user experience handbooks:
What You See Is What You Get:
- When a user clicks on a link whose target URL is displayed by the browser at the bottom of the screen, she expects to navigate to that same destination. In a case where redirection happens afterwards, as a consequence of the click, the user expects to remain within the same domain of the displayed URL, or the website she is on at the moment of clicking.
- If an object is clickable, but the browser does not show any domain at the bottom of the web page, a user expects the click to generate some action within the current website and not to navigate to a different domain (as defined by the World Wide Web Consortium).
- The user does not expect any external navigation to take place when she clicks on a non-clickable element of the page (such as a simple text paragraph).
- When the user clicks an HTTPS link, she expects that the communication towards the target URL will be encrypted (no information sent in plain text).
Trust in the Endpoints:
- If a user on a website A clicks on a link to a domain B, she does not expect any other domain, apart from A and B (or those included by them), to execute code in her browser.
- If cookies are created in the process that follows a click, the user only expects cookies from the domain she clicked, or from any of the third-party domains included by it.
- If a new tab is opened by the browser after the user clicks on a link, the new tab should not be able to interact with the other tabs already open in the browser.
Stepping into the Future of Click Transparency
In our assessment, we identified several examples of bad practice with respect to how click-related events are managed by existing websites. We hope that this work can raise awareness about the widespread adoption of misleading links and click-related behaviors which could leave users vulnerable to security risks.
Ultimately, we cannot expect all web pages to follow the click contract point-by-point; therefore, introducing a line of defense to help protect the end-user is imperative. To that end, the Norton Labs is working towards implementing tools (e.g., browser extensions) that could help prevent these potentially risky side effects. Stay tuned!







We encourage you to share your thoughts on your favorite social platform.