How Did That Get in My Phone?
Unwanted App Distribution on Android Devices
Android has become the most popular operating system with over 2 billion active devices and over 70% of the mobile device market share. A major reason behind Android’s success is its open environment that allows affordable access to new app developers. Unfortunately, popularity and openness come at a price: abusive developers also have easy access to the ecosystem allowing them to distribute unwanted apps such as malware (ransomware, banking trojans etc.) and Potentially Unwanted Programs (“PUP” like adware, rogueware etc.). Cybersecurity firms keep reporting ever-increasing numbers of unwanted app detections and collected unwanted app samples.
A fundamental question is how these unwanted apps find their way into real users' devices? What is the role of the official Google Play™ store and that of other popular alternative application marketplaces? Are there other types of apps with install capabilities and what is the role of those in unwanted apps distribution? In a study we performed together with researchers from the IMDEA Software Institute, we seek answers to these questions by analyzing the who-installs-who relationships among apps in over 12 million real Android devices. The results of our study will appear at the 42nd IEEE Symposium on Security and Privacy (S&P) conference in May 2021.
Is Android Safer Than Windows?
A common belief among users is that Android is safer than Windows and thus it is more difficult for unwanted apps to find their way into users’ devices. It is true that the Android ecosystem has implemented many important security improvements over the years including OS app isolation, the OS permission model, and the official Play store where apps are required to pass Google’s vetting process before they become available in the store. However, are these defenses enough to pose a barrier to entry for unwanted apps?
We use our dataset to measure the number of devices with at least one unwanted app installed. Even our most conservative estimations find unwanted apps installed in 18% (2.2.M) of the devices in our dataset. Our estimation is comparable to the unwanted app prevalence found in Windows enterprise hosts [1]. This indicates that, although Android defenses pose some barrier to unwanted apps, a significant percentage of such apps can circumvent it, highlighting the need for additional security layers. The constantly evolving Android threat ecosystem is catching up in size and complexity with that of Windows.
How Unwanted Apps are Installed on Users’ Devices?
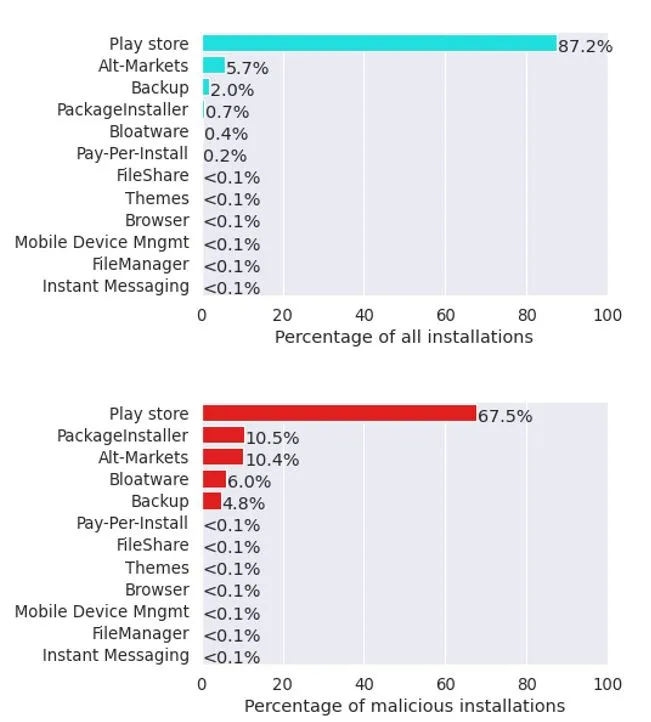
We analyze how unwanted apps are installed on users’ devices by examining the who-installs-who relationships between installers and the installed apps. We compare unwanted app distribution vectors by classifying the installer apps into 12 categories: the official Google Play store, alternative markets, browsers, commercial PPI services, backup and restore, IM (Instant Messaging), theme stores, file managers, file sharing apps, bloatware, mobile device management (MDM), and package installers. Figure 1 depicts the fraction of installs delivered through each of those 12 distribution vectors over all install events (top) and over unwanted install events (bottom). Some of our main findings are highlighted below:
Google Play™ Store
We observe that the Play store is the main app distribution vector responsible for 87% of all installs and 67% of unwanted installs. Although only a very small fraction of the apps distributed via Play store is malicious (0.6% of the APKs), due to the market’s popularity, this translates to a sizable percentage of malicious installations. Thus, Play store defenses against unwanted apps work, but still unwanted apps can bypass them, making it the main distribution vector of unwanted apps. Despite that, the Play store remains the less risky distribution vector.
Alternative Markets
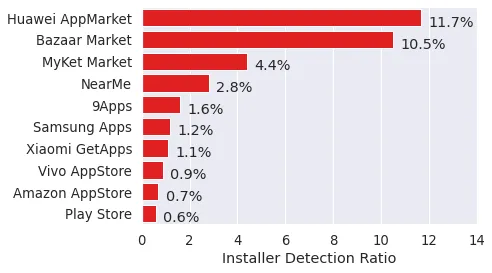
Alternative markets are responsible for 5.7% of all installs and 10.4% of unwanted installs. However, on average they are five times riskier than the Play store. As Figure 2 shows, the download risk highly varies among alternative markets. Some like the Amazon Appstore and Vivo App Store are as safe as the Play store, but users of other top alternative markets have up to 19 times higher probability of encountering an unwanted app.
Package Installers
These largely correspond to manual installs by the user, who may be consciously installing unwanted apps that offer desired functionality. For these installs, the vector through which the user downloaded the app into the phone is not known.
Backup Restoration
Backup restoration is an unintended unwanted app distribution vector responsible for 4.8% of unwanted installs. Cloning of apps during phone replacement can facilitate unwanted apps to survive phone changes by the user.
Bloatware
Bloatware, pre-installed applications with questionable functionality, is another surprisingly high distribution vector, responsible for 6% of unwanted installs. This is likely due to ad-based monetization by device vendors and carriers of the devices they sell. Bloatware installers are often privileged, making their removal by security tools and users challenging.
Browsers
App downloads from the Web are rare, <0.1% of installs, but have significantly higher risk than downloads from markets, even alternative ones.
Implications for researchers and consumers
Our results confirm that future research should keep focusing on improving the vetting process of Android markets (official and alternatives) since these are the main distribution vectors of unwanted apps. However, our research also reveals a complex installation ecosystem with several surprising distribution vectors like backup restoration, bloatware, themes, file managers etc. Although some of these types of apps are expected to perform installations, most are not. Further research is also needed in the space of privileged installers. These installers have system level permissions and cannot be uninstalled by normal users or security tools. It is worrying that privileged installers are responsible for 9% of all unwanted installs (but only 4.1% of all installs).
Our findings question common beliefs on Android’s safety and indicate that additional security layers may be required for improving the security posture of those devices. For minimizing the risk of exposure, we make the following suggestions to Android users:
- Try to install apps from the official Google Play store. If you want to use alternative markets, prefer those that apply sufficient checks against unwanted apps (check Figure 2)
- When replacing your old smartphone and want to clone your apps to a new phone, sift through all installed apps and discard any unused ones or those that you were unaware of their existence.
- Always be cautious when apps propose to install other software, especially when this is not an expected behavior from the original app. If unsure, abort the installation completely.
- Avoid installing apps that you randomly find on the Web or receive on Instant Messaging apps and social media platforms.
[1] Kotzias, Platon, et al. "Mind Your Own Business: A Longitudinal Study of Threats and Vulnerabilities in Enterprises." NDSS. 2019.









We encourage you to share your thoughts on your favorite social platform.