Disguised Malware Distribution Techniques
How attackers leverage fake software websites, search engines, social media platforms, and social engineering to deliver malwares
There are many ways to spread malware to end-user machines. For consumers, one of the most commonly encountered and unfortunately successful attacks is social engineering. That’s where the user is tricked into allowing the malware onto their machine, or even actively installing it themselves.
To do so, the attacker must not only present a convincing case to the user that the malware is legitimate and benevolent but also bypass any security mechanisms that would interfere with this scheme.
Researchers from Avira, part of NortonLifeLock Inc., have been tracking a long-running campaign that specializes in distributing malware through what appears to be cracked, or illegal, versions of various legitimate software. Such versions are served through web fronts that act as intermediaries and give the impression that the downloads are legitimate – at least as legitimate as a software cracks can get.
The campaign appears to serve many different crimeware groups and can deliver many different malwares.
Later in this article, we have detailed the adoption by ServHelper Backdoor Dropper.
Methods
The first and foremost place where users look for cracks, game trainers, game mods, or license serial numbers is on Google or other popular search engines. From an attacker perspective, it’s desirable to get into these top search results so that the user is driven toward downloading the malware.
To achieve this, the attacker employs what is known as SEO – search engine optimization. There’s nothing nefarious about this. SEO is a common practice for gaining more visibility on the web.
The attacker download sites are being made visible through the creation of SEO-friendly tags, as well as by creating multiple pages with popular software tags. This enables these highly malicious web sites to show up near the top of a regular Google search.
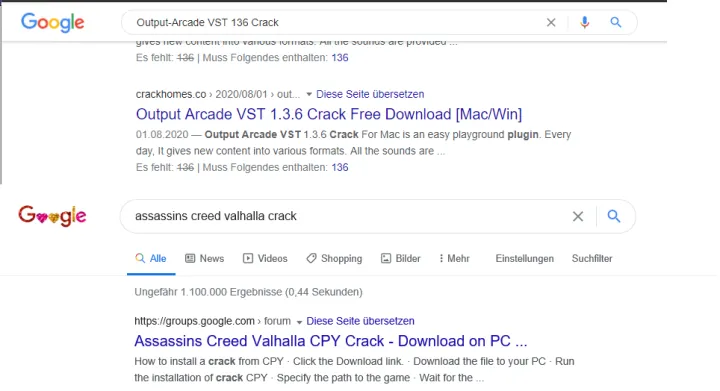
Web delivery:
Most of the final payload — the malicious code — is not directly accessible. The user needs to click through one or more web fronts that are designed to look like the type of semi-legitimate websites that might host cracked content. These frontline delivery pages include entries on popular social media sites like Facebook, Twitter, Reddit, and YouTube.
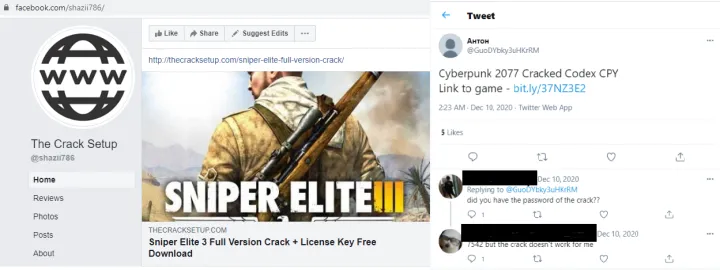
The main purpose of these frontline pages is to serve the download URL to the final payload or sometimes to link to another intermediate custom-designed fake website hosting the final payload.
Depending on the crimeware group, intermediate pages may or may not be present. Some groups are extremely cautious about not getting the final payload delivered into antivirus companies’ automated crawlers or other search engine crawlers. So attackers add additional scripts to check that it’s a real human trying to download the final payload. Those methods are discussed in detail later in this article.
Intermediate pages are usually hosted either on free hosting services or on private domains purchased by the attackers.
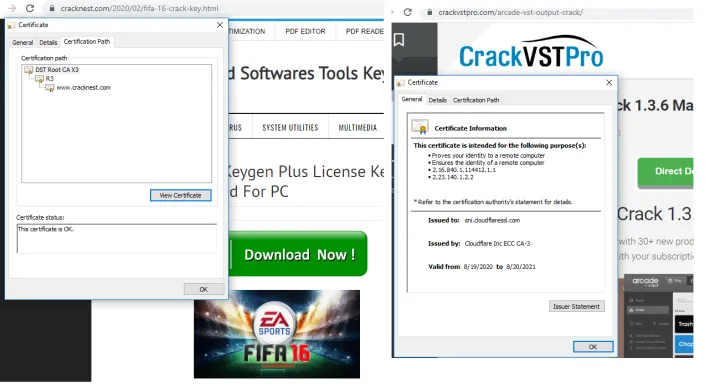
Which hosting services are used vary and may depend on the crimeware group. Registrations are privacy-protected.
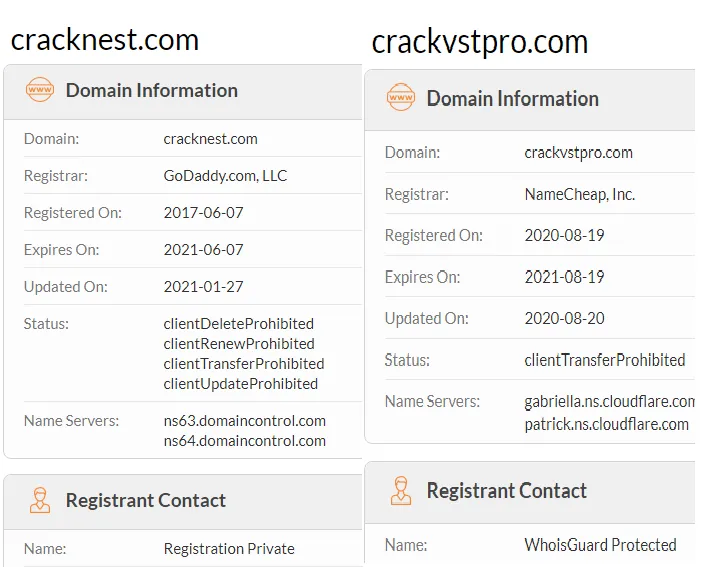
We observed attackers heavily abusing legitimate free web-hosting services like Weebly, Google Sites, Wix, and Google Groups. An advantage of using free webhosting services is that attackers can also leverage other free services provided from the vendor like SEO, which will add value to attackers in hitting top search engine results.

Anti-Analysis Checks:
Before delivering the final payload, the intermediate pages are also responsible for some anti-analysis and anti-crawling techniques. These methods may differ between crime groups, but the final aim is to avoid automatic downloads by crawlers and malware collector machines.
Referer Check:
Requests to websites normally contain a referer field. This identifies which site the user came from before arriving at the malicious page. The attackers check if the referer is a popular search engine before proceeding further. This will filter out many automated crawlers.
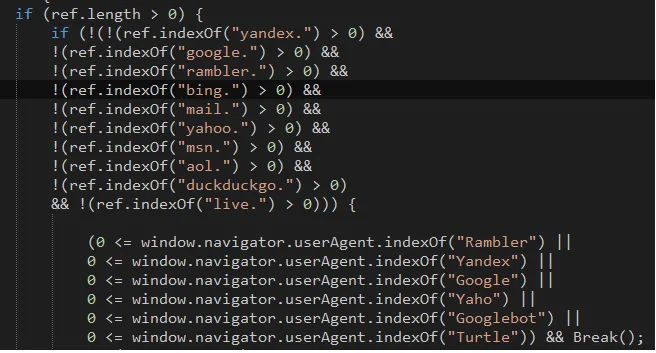
List of allowed referers are
- Yandex
- Rambler
- Bing
- Yahoo
- Msn
- AOL
- Duckduckgo
- Live
User-Agent :
The next check is User-Agent. The User-Agent field is meant to identify which process sent the web request (normally a browser). However, if the User-Agent matches any crawlers or bots, the attacker will simply skip delivering the payload. Below are User-Agents that are blacklisted by the attackers.
- Rambler
- Yandex
- Yahoo
- Googlebot
- Turtle
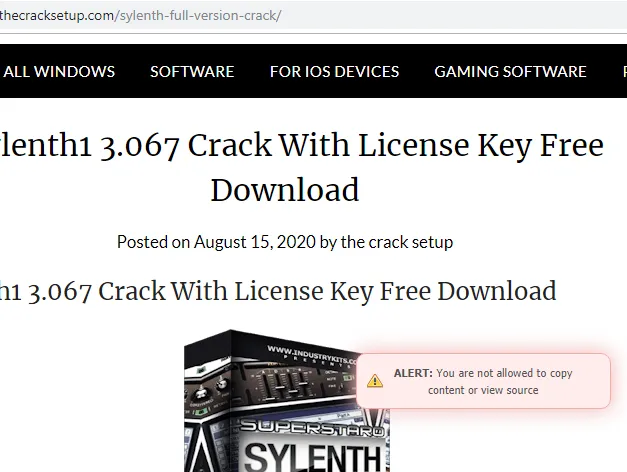
SourceCode View Protection:
This is a simple analysis-prevention trick where the sourcecode of the website is blocked from viewing through a browser. This is done by using a keyboard shortcut or through the context menu and is presented as an Alert message. Source code can still be achieved by alternative methods.
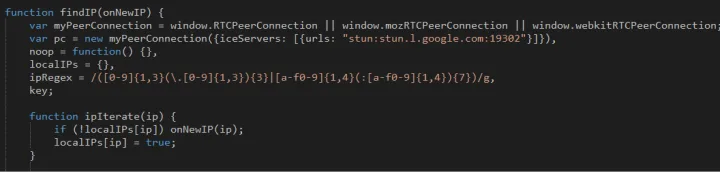
IP Filtering:
In this method, the attackers will not deliver the payload to the same IP address again. The motive behind this is to avoid any other crawlers that bypassed earlier checks. Another motive may be to track victim counts based on geography. One crime group leverages a Google STUN server to determine a victim’s externally visible IP address.
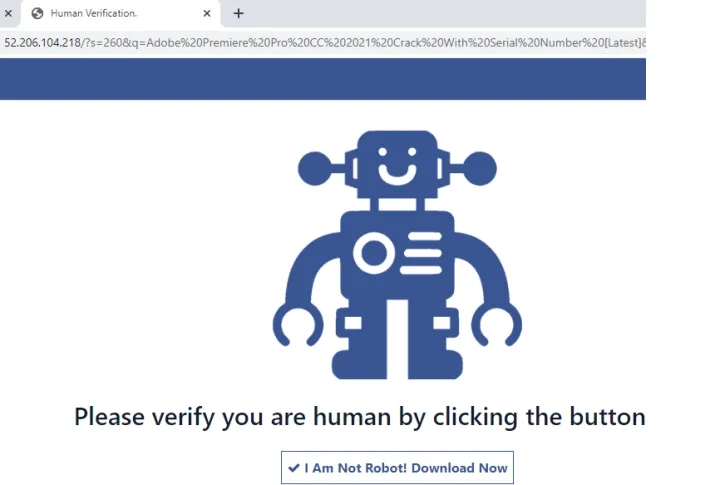
Captcha/I am not Robot :
Some crime groups implement “Captcha/I am not a robot” functionality on their pages. This is yet another way to avoid crawlers and perhaps help make victims believe the page is legitimate. This was usually the last check before delivering the payload.
Password Protection & disabling antivirus:
When the payload is finally delivered, it is usually in the form of a password-protected archive. The password will be part of the delivery or will be separately displayed. In most cases, they are not connected together. This is another way to avoid robots from getting the real content. Connecting a collected archive and a password delivered separately is hard to do automatically.
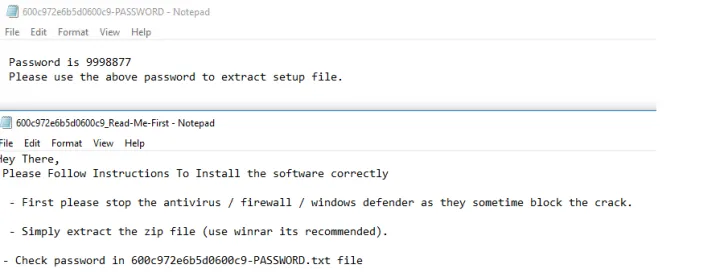
The final payload may also display instructions to the user to turn off antivirus and firewalls. This is a social engineering technique to trick the user into installing malware without any complications from the security software. This can be a very effective technique as we have confirmed with telemetry.
Payload:
Payloads differ based on the crime group involved , so far we have seen a mix of different malware ranging from highly dangerous ransomware, backdoors, and information stealers to potentially unwanted programs and unwanted browser extensions. Each crimeware group has its own metadata pattern that they follow for a certain period of time. For example, some may have a pattern in payload naming, the filetype format they use, or specific password selection across different payloads.
Below are some of the recent naming patterns, and most of them will be present inside password protected zips
setup_x86_x64_install.exe
setup_install.exe
SetupFille-v34.0.2.exe
32_64_ver_1_bit.exe
MainFile-v21.5.02.exe
Tsetup.exe
<popularsoftwarename>-_<9 digit>.exe,example: adobe-_128022649.exe
<popularsoftwarename>_<9 digit>.exe,example: excel_829982821.exe
<4 digit_SETUP.ZIP> -malware dll name inside will be msimg32.dll
Some families that were regularly detected were Download Assistant, CoinLoader, Redline Stealer, Predator The Thief, CyberGate Rat, and ServHelper backdoor. Most of these payloads are well-documented.
But, while analysing the ServHelper backdoor dropper, we came across its adoption of Alternate Data Streams (ADS) and the bundling with a legitimate Telegram messaging setup.
TA505 ServHelper Dropper Adaptation - ADS & Telegram Bundling
While checking telemetry of victims from malicious websites, we noticed a RAR SFX sample, which in our cloud sandbox dropped further files in an Alternate Data Stream (example hash : 0d898368a1d4e605e15963dfeaf87cdde82107a8a158743b5753dec961d2872e). This was found to be a ServHelper backdoor from TA505. ADS is always an interesting trigger to dig into further, and later investigation revealed that these RAR SFX files were coming from two different sources:
- Installed via an initial infection from Download Assistant family, (example hash: 247d92f74a4d6f944cc7fa3f3b88872667ff405c758cb1c4da54fad98ac01f9c) which came from the above-mentioned fake crack websites.
- Installed via a CAB SFX filetype bundle, which bundles the Servhelper dropper and a legitimate Windows Telegram Setup. This is commonly archived and spread by the name tsetup.2.5.1 (example archive hash: ada6c389df1c10f170e50d4512e0d6b97eff06b94039aa860dae657ee202deda). The name is chosen to mimic the real Telegram setup.
Telegram Bundling:
As mentioned, the bundle is a CAB SFX file and uses two CAB SFX commands:
RUNPROGRAM – This command is used to execute the legitimate Telegram Setup. POSTRUNPROGRAM – This command is used to execute the RAR SFX mentioned below, which drops the ServHelper backdoor.
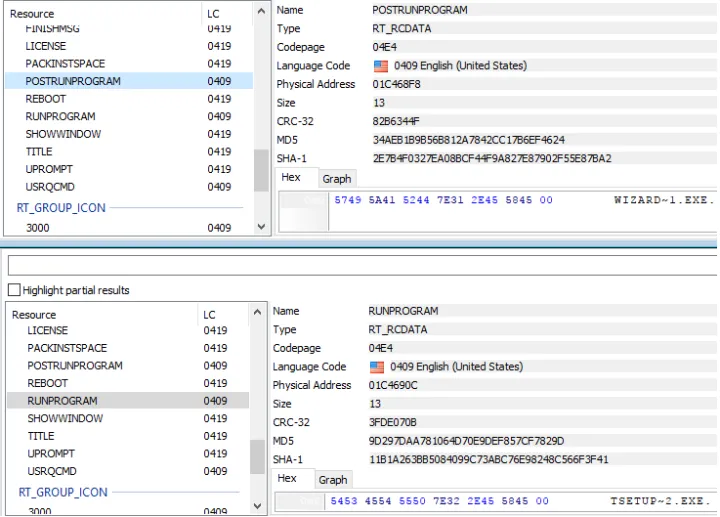
This bundle was mostly hosted in discordcdn. This is the file-hosting service of the Discord chat platform, which attackers have recently abused as a malware-hosting hotbed. Another dropper was hosted on hxxps://tsetup.net/tsetup.2.5.1.zip, mimicking the hostname of the real telegram setup.
RARSFX Dropper
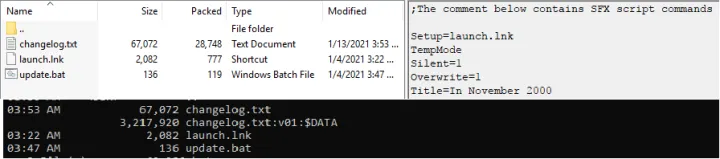
The dropper RARSFX mainly contained three files:
- Legitimate file with the ServHelper dropper stored in DLL format in its Alternate Data Stream
- BAT File – This starts the DLL in the ADS using files using rundll32.exe
- LNK file – This points to the BAT file
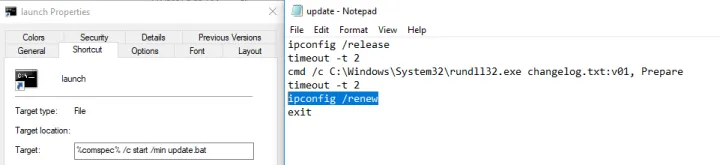
The Setup command from RARSFX is used to start the LNK, which triggers the bat and finally the servhelper backdoor dll in ADS using Rundll32.
An additional task of the BAT file is to release and renew the IP address of the adapter.
The malicious DLL is a 64bit UPX-packed executable. In its unpacked state it’s a Delphi-based wrapper. There were no other behavioral changes we noticed from the second stage – it was having the usual ServHelper Powershell Script, UAC escalation via SilentCleanup technique, the copying of wscript.exe, and maintaining persistence via TermService ServiceDll.
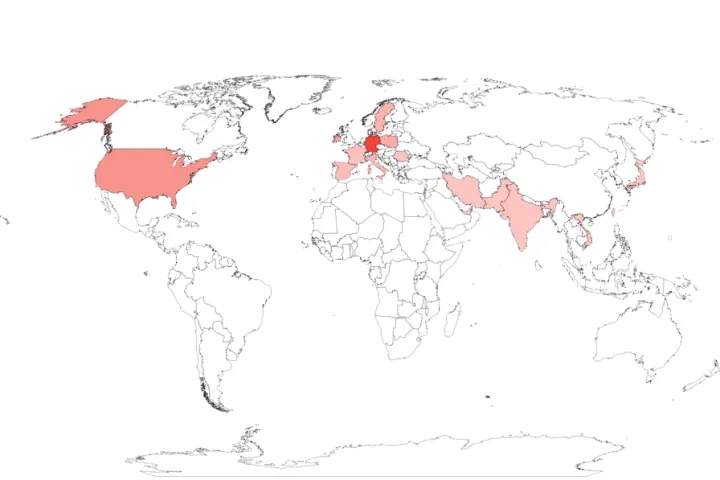
Based on our telemetry, the victim geography of this ADS-based ServHelper backdoor was spread across the United States, as well as a few countries in Europe and Asia. The earliest sample was from November 2020.
Conclusion:
Spreading malware via fake cracks is not a new vector in malware distribution, but recently the number of distributors is alarmingly high. We believe social engineering tricks still work far too well for getting access to consumer machines.
Most infection scenarios involve victims being lured with an entry point like a spam email. But here it’s reversed — victims go looking for content themselves and fall into a malware trap.
These fake crack packages used to install adware and PUAs — short for potentially unwanted applications — most of the time. They’ve switched over to real malware like Trojans, Backdoor, and Stealers, and they install a lot of different families. This results in badly infected systems, if the user falls for the social engineering.
You should never turn off your security solution based on instructions from a website you don’t implicitly trust.
We would like to thank Snorre Fagerland from Norton Protection Labs for the support he provided us during the research.
References :
https://attack.mitre.org/techniques/T1564/004/
https://www.avira.com/en/blog/ta505-apt-group-targets-americas
https://www.avira.com/en/blog/coinloader-a-sophisticated-malware-loader-campaign
Indicator of Compromise:
SERVHELPER RARSFX ADS DROPPER(BUNDLED With TELEGRAM FILE TYPE CABSFX)
17753d59a4cc7105e24c33c09b095c9b888879576d8744829e1ece6fb20e5108 2721a2af5df5962164229cc9a9c649ac1729b81de4fdd655a58660655038a779
a88285c387c4cd5d3d5319f2b02aea0473539ff37e8b545c81c4dcba283f05a8
RARSFX ADS SERVHELPER DROPPERS
6daa8b17b862f0458117c191d6a7f89109a3b2a6e00f688aa2340bfb264bdd08
b59fb6b5b237618677d7dac2f9a442c4d9ea3ddf325fb17475dfa1533cb13874
4cd8dd3c3c0065d66e0438ba477011872176f6eca30090a8be91d5ad1ca636aa
9dac8e5f93efeba219860f6f244ffa629f6e999b4c63357b00e94f9a797b5ac4
a70d709888225f07022a57f0d234b3bddae9d46e6f99d2fe71b8d68571e465d0
727dd175679f1e027a53d98b432fee4350441d113c95c26bee9897d529dde871
f32a9515113c92f58f9137a688914906210450cdd627b8a520d1b75e70b0ab08
cef4073dc2af79b24983173244f138254c9e1a64271f496b21433938f39cd66e
91b44476331dead0d79573a2aa386063d5acb4dab4f592bb393fb4956fb628d0
1f6f6697e6b32d63ad87ef1c321b27c27ad5254e60f06d400e326fbbaedaf1c5
02d9ab65fac2a75e17e8631282278efe732bf68bea0d3836f6d256c6d5c5e173
bb2efa8daabf4f6feaaa48e842e2ea854dd04eb83ceff74ea54607fd0c51aada
7dae31a4e314868e975689504629d94c59d359b7b159a9a99f3ab13721ce5cd0
8345bf3e9dae0a447bc1c65c99fa0e102e7f0f3fd77f137cc5c876ceb2a647b7
d06d7b5c4613a3d9fa020854878558325da6fd932f74b8268360d4838286d43c
10892007582c3c09a01a4de7ac9e2ca434704396e5cc899f26c9f83a626da2b5
f8e51b2f994a7436d6dfaa1afcbb34e5f261914078283306213902c7d973b9da
f823dbbf95afe26ef6b967d10a00306ec3d00027c13b600ce873888144822668
863726489ecd301121060d07724915b0feb4320b63e2767a47dd3e683e578478
6eb8dc792f4b986a01cc1b49bb5f4fdda827d6050fda9db640edbc20b6f5fc5a
7ba20f005647c60094216cf79f23a07b2fc507392163d57679266e4f4b81148c
334ee3b667aaf34a2ec9ae2f9f920124e68c05433c8ecd679beaa89d9698d017
0d898368a1d4e605e15963dfeaf87cdde82107a8a158743b5753dec961d2872e
b2d5c20338729ba2a81dd35c662adb978f07eb5857feaf170aa34f505a26cd9b
218acab1911a2d7a3be5d2dc118fcd97390070af6a6c8340b83d103efc3d3158
c91bd2607bce8a505ce213ca98f230c714791cbbedd8399831f94f14fd3d646e
bc1a36908ae82f0ad6877a4156485a3a081ab2350dc62b2aa6103849bfd8b070
c99206b8cd8cb64fc9d268c1cbbf545a6126cafaa999bddf4d4d6b4fc6942023
c5d8937059b026638e38ab486d29c80ae86ee3e4ca5d03b26f929c6e59c93e27
4abf7e1e0c1dc064cf01290736dce81433206a0b9a13673f6c0f9dd9340a7318
f62d5218958cc57e5306f264414fc026b77e7c0a5c8b86740855bb1dccad618e
862f4fb394704621cabf8e06d70d26ef76a4a38215f3d104b99ef7a5eb23c3c7
c21c491c2eafda1c7c168cfdbbe2e9264dc9e3417e9a8dc60a3cbd8c947e98dd
d2dca4f0b96c99217419939f6ce0ceeb7a96b725a4325aacbcd728de3c9b6760
3f53ef55ad98ca965b96ba51205e06780b6d269e62cf56b3867ddf505b1aea9e
66ee804ec888743457a62d504b34c23bf4d74faa8502b333ebdccf745fef7881
bb98f94b6a77d50e057ccde92c1ad2831f7fcaa7c7a08e4e07930e94ee828bce
b24493f77bb5eb632106210c3ae4daa494688a8f1bec429fbea4a6200c4ed980
eea71fa77ef78f1529f548e28805198527d2ba5f5d0fbcfa1cbf64be8bbdad68
31ff256ba95fc83aa386fa7e7f63c9c2c227b927cc213f63e1a11eb62db1b9bf
90cf7c91d7bd048650b626b55322473a1afb5ea830bfab1bcef16f4cec4f9d2e
a0b4d6de64dc287366934ad498b048d5a4ff3a750633d57053861722fae9411a
3c94b860387a5222d1236a76d6f7b728f7acf9ec427ea7ae25e0119eed7b0ae2
6d3da4767436fd91be867be94ee34910e727319583d381e0abf84116d89c37ae
0ad4b514e45536d536861dccc3968fb8f5e7f7e5a6fee7ea8b03f3b8a41f1d50
0b2fc45f1a30cd367bcfe4d450b7f7e5ddee7e27f27f50363e86b09833162d23
95fe8e3a0b0f473651d93142d4c8c0a5c87d6179ee077727f3bddcedd4317d70
1638f8b3579cbe5b9f592f546adb6a2e3147f063a1c0934e73e9b84572e21660
bf2b54807e0c5a2806308d14e1c4cc6689f20d0347d84b5bbf15ba2924dd6569
a28eaed67d0fb610aa6d09e3b1d68504ca92528028fa2b58e19cbc04858911fd
4011ec9abd80425b6aff8e3f19822a12e099298a3bb93798e207a2ee82cdd290
76bd8b7517ce06d48dd8336f6c881408982cd05943f139f2ad354ce73394b87b
13c0fcb55e1b7057c00ae4b1c7acdd6939fe343c426d6b046b4950fa97e8f70d
8f30f4d4107af891f4433983808ee7adffd1b59f83cd78cd1c95aced73f83ba7
92770e4e6008c576cf162e679205652e982f233bbfaa46c73d46ece80a5f25a7
774c12bb309d48fea2cb5e2b8f515cbb1f2e15e121969c3aee05724c4e8b0d28
1d88a6c77e4d5f8a3657cb936cb9997fbfaf8be39f2fe94963ac24014477fb9b
14b64685016511348bd7e42097e401e85794d484a7f6f03645155c53355856f8
d897a131bc428cc9c5a2dad34ad10587026e9f43bf8021109d474d2462b15b91
56458d4bbca081d3113bd16edff03a52565e2af8c80ecac06fcb2fd907c094ed
5d06f0841ce9aab66203e47740f2cc91631d98768e9aa791eafff03c8de7addb
0edd68c1d3cf2032168f9defce868a67a5e7ab859bd444504bb35159fd266958
ce393f37394335fb9eb6186d1eebb1c4eb0c6561cdd9b1be61b794303d681a46
1b0ca2e821002bd2871b6f00340625e3a43079f5135af91ccaf0eb1e8f4e9871
b75b2f353508add64274d16d121acea4a38a9def8c5cc739d0952f8fdd5a0755
78fe7e8d912795cfd914ee8de8bdedb1508179c4b17bed2f5e78a3db005e6ff3
3a2ea2f8ea3b056461a45e20223361a4140832aecdd9109dd2be655afb08d093
90f0f5bdf3d9fb4f5cf84f168987f72f8d7cf36d73afed27b2c080c8fb36baf6
663d6cfa45cc32fea1fd4e64025ed42f4d059954c92d4dfdf05064046586ab7d
04dfcbdc54bb918528ffdbb49d8edce05891eb325d60c958c9a811796cba7fca
9fbe0b3757f4a4c6ab62633e8fefdf5052a953dff06f98bdc39114a49c07bed6
3fbbc43d7acd34ac3d3aa717ab0649d07670023fb6961445099a1e9812eeae84
8e6f7f9be35e856c9bb2b7936106b313fa6f9eb7a9f37531243147b27ae142e9
86ab50479adcbc20d73d7c9255e5447b743d93ab0ae33710c557556e973c9513
ad919af1a4d66e6d8aec5c4beed7660e938a70f3f6286a4c808dce01730cbed5
6f5a77c208c465b2dee98e441783e3cf7ab48dd1d4dce06131f794cec4e6920e
7effa33451e068a190327fa5a90de33b6a56925da64a4b75f8bc067a850a9bc7
85a6195168a9a243adb0126d331ac5b5eb4b5f22ca97569534de26d5aceca1f1
c571f2f536cb956e3dd67af86a02070701b6afaf83e03313e47471719ae224a6
2c8ea0f991d74146f056e4ed453e92ad1798daf2878f5520f54cf3d70d607613
721020c2fe25c248dd28cabdb329cbd1b97a213495ff381732661b8d6e40a1ee
94e38ab6bdcf6e3c9e7780353f157353a38501041b94c79f6887784eb3738839
db0ef9f64e3e45cfaaf256d896741fdd0c3b51230a5ac9fde487493cb23c7a90
f9e85d688ecf9ed58b36a860f700ea5a941da891c502e9e48589cb0028909d5e
6b9889ca12fec97177657b96a912ec0d43580aee52958a7bedb065c4f8b18dd9
URLS:
hxxps://tsetup.net/tsetup.2.5.1.zip
hxxp://cdn.discordapp.com/attachments/799041323864424468/799805557434220544/tsetup.2.5.1.7z
Fake crack websites, listed below are few of them only :
hxxps://crackvstpro.com/
hxxps://www.cracknest.com/
hxxps://skyeyload.weebly.com/fifa-crack.html
hxxps://sites.google.com/view/working-adobe-premiere-crack
hxxps://groups.google.com/g/vallhala
hxxps://chaywarbworllosper.wixsite.com/sobunperdcuc/post/vrs-tacpack-fsx-crack-download
Innovations from Norton Labs are for research, evaluation, and consumer feedback purposes. NortonLifeLock does not give any warranties as to the suitability or usability of these prototypes and recommends safeguarding data and reviewing all terms and conditions before use.
Copyright © 2021 NortonLifeLock Inc. All rights reserved. NortonLifeLock, the NortonLifeLock Logo, the Checkmark Logo, Norton, LifeLock, and the LockMan Logo are trademarks or registered trademarks of NortonLifeLock Inc. or its affiliates in the United States and other countries.







We encourage you to share your thoughts on your favorite social platform.