Mercenary.Amanda
Professional Hackers for Hire carried out large-scale credential spearphishing campaigns since at least 2013
After an in-depth investigation of a wave of phishing attacks by the threat actor Mercenary.Amanda, we conclude with high confidence that operators at an IT company based in India are responsible for performing account intrusions at the behest of private investigators and other clients. Mercenary.Amanda has been executing persistent credential spearphishing against a variety of targets in several industries around the globe going back to at least 2013. Symantec, now NortonLifeLock, gathered attacker data and telemetry that built a detailed picture of the phishing operation and campaigns from late 2017 to early 2020.
During that time, a total of 220 identified target organizations around the world with over 1,800 individual targeted email addresses were observed. Tight clusters of verticals in the phishing attacks suggest motives of financial, industrial as well as political espionage. The target list assembled during our investigation indicates campaigns against environmental advocacy groups, investment businesses and financial journalists, law firms, and political consulting, as well as dozens of individual targets that do not bunch into one of the categories.
The EFF published a blog titled “Phish for the Future” in September 2017 that detailed spearphishing attacks against two non-profit organizations that link to the actor that we track as “Mercenary.Amanda”. Our name for this group was derived from the apparent motivation of hacking for money and the email alias amanda.lovers[at]mail.com that was heavily used by the group to register phishing domains in 2017.
Closely tracking the attackers’ actions from domain registrations and server infrastructure allowed us to discover unique threat data including phishing kit source code, server log files, and documents that the operators left behind. The scale and breadth of the phishing operation against completely different industries, geographies and individuals implied that the actor contracted as a hack-for-hire operator. Following several operational mistakes by the attackers in 2017 and 2018, reasonable evidence was gathered to directly attribute the Mercenary.Amanda operations to an IT company based in India that advertises “Cyber Intelligence Services” to private investigators and corporations.
Hack for hire
While it is still possible to find and hire hackers on an underground forum like in a stereotypical movie script, today there is an industry of hack-for-hire companies with complex business relations. These companies advertise virtual “intelligence services” and are used by their clients to offshore the hacking of targets to countries with low risk of prosecution.
Collaboration & Notification
During the course of the Mercenary.Amanda investigation, the NortonLifeLock Labs team learned that researchers at the non-profit Citizen Lab were also working on analyzing the campaigns, leading to a research collaboration with mutual sharing of threat indicators and investigation results.
The report into the actor called “Dark Basin” by Citizen Lab can be found here: https://citizenlab.ca/2020/06/dark-basin-uncovering-a-massive-hack-for-hire-operation/.
NortonLifeLock has shared relevant technical information to law enforcement agencies in multiple countries to support respective investigations.
While a public report was held back until now, our team has been working to notify targets of Mercenary.Amanda phishing campaigns since early 2018.
Indicators
A list of domains used in the phishing attacks were produced as a joint effort by researchers at Citizen Lab and NortonLifeLock Labs and can be found here: https://github.com/nortonlifelock/indicators/blob/master/mercenary.amanda.txt.
Credential Phishing Operation
The phishing campaigns executed by Mercenary.Amanda have been following the same pattern: spearphishing emails are sent to individuals at the target organization that include a link ultimately leading to a credential phishing website operated by the attackers.
The email attacks we observed generally followed one of two techniques:
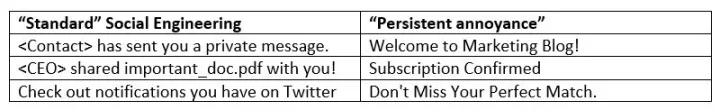
- “standard” social engineering that mimics notifications from online services,
- emails that are meant to persistently annoy or embarrass the victim.
While the mimicked notifications are enticing the victim to click, the latter approach aims to deliver something to the user that they do not want to see in their (work) email inbox: newsletter subscriptions or sign-ups for dating or adult websites. If the victim in this case clicks on an “unsubscribe” link, they will end up on a credential phishing website set up by the attackers.
While the mimicked notifications are enticing the victim to click, the latter approach aims to deliver something to the user that they do not want to see in their (work) email inbox: newsletter subscriptions or sign-ups for dating or adult websites. If the victim in this case clicks on an “unsubscribe” link, they will end up on a credential phishing website set up by the attackers.

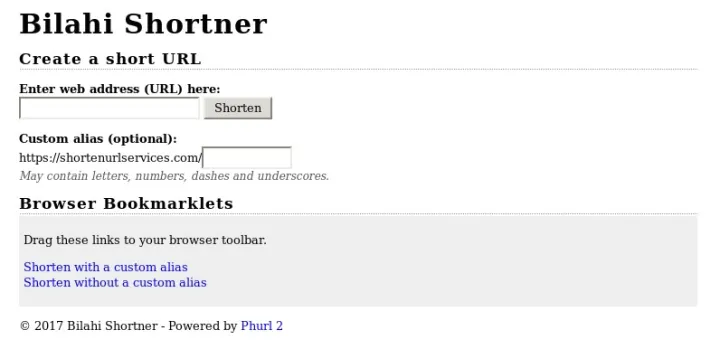
The embedded links contained in the phishing emails do not directly point to the credential phishing pages. Instead, the attackers have set up their own URL shorteners infrastructure using the open source project “Phurl2”.
The effective landing URLs are customized for each attack and include information about the target in query parameters. Following is an example of Mercenary.Amanda landing URL:
https://tricktravelbooking.com/account.login.system.gmail.com.appredirects.portfoliofa.system-login.app-direct-signin-login.ppsecure-auth/?email=<redacted>&error=Sign in to continue&redirect=//support.google.com
In this case the URL includes query parameters for the targeted email, an error message displayed on the phishing page, and a redirect URL that is used after credentials are entered.
Mercenary.Amanda has a large arsenal of phishing websites ready to deploy depending on the accounts targeted in the attack. During the investigation of the recent campaigns we found 68 website designs copying popular email & cloud services, social media accounts, and a number of customized phishing pages aiming at organization-specific services.
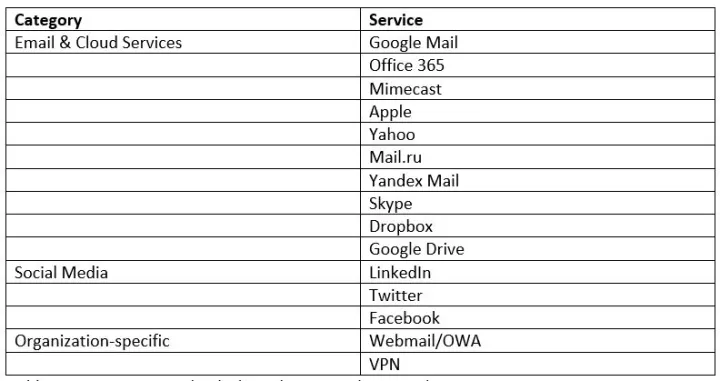
The respective websites also seem to have been localized depending on the victim’s origin. For Google Mail, for example, variants of the login page in the following languages were found: English, German, Spanish, French, Portuguese, Icelandic, Hebrew, Italian, Romanian, Russian, and Ukrainian.
In multiple cases the Mercenary.Amanda operators left behind ZIP archives that included server-side PHP phishing code and log files from previous deployments.
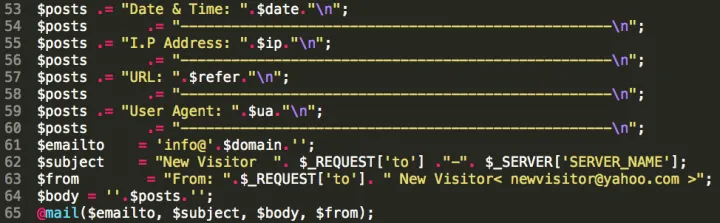
In 2016 and 2017 alone, the attackers registered 248 domains for the credential phishing operation. During that time, registrations were mainly done through two email addresses: amanda.lovers@mail.com and amanda.kruetner@mail.com. This changed in December 2017 when domain registrations were switched to privacy-protected at the provider.
Targets
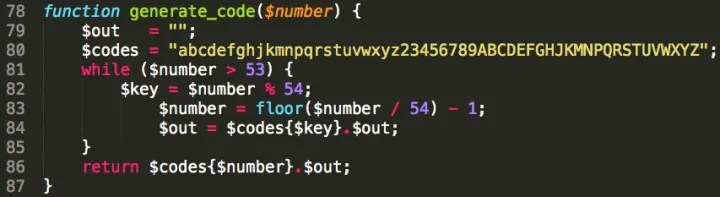
Examining the PHP code of the open source URL shortener “Phurl2” (http://code.google.com/p/phurl/) used in the attacks brought an interesting detail to light: If the user does not specify a custom identifier, the application generates new shortened codes in ascending length and order using an internal character array (s. screenshot).
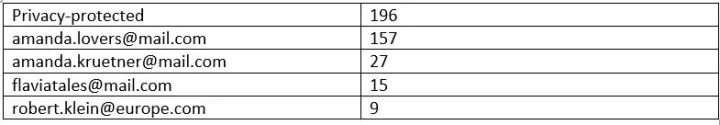
This discovery allowed us to enumerate the shortened URLs and capture a list a total of 5,311 unique landing URLs used in the attacks between 2017 and 2020. Embedded in these URLs were 1,886 target email addresses and hundreds of subdomains and paths where phishing pages were deployed.
Using this list of email addresses, we were able to establish a detailed picture of the phishing campaigns that Mercenary.Amanda executed during this time window. Over half of the addresses pointed to corporate email accounts and allowed us to identify 168 targeted organizations.
For email addresses observed in the enumeration more than once, the average length of attacks was 32 days, while the number of attacks per address averaged to roughly 5.
Many individuals were targeted using multiple email addresses, including: work email, university (alumni) email, personal email (Google Mail, etc.). In multiple cases, family members of targeted individuals were also targeted at the same time.
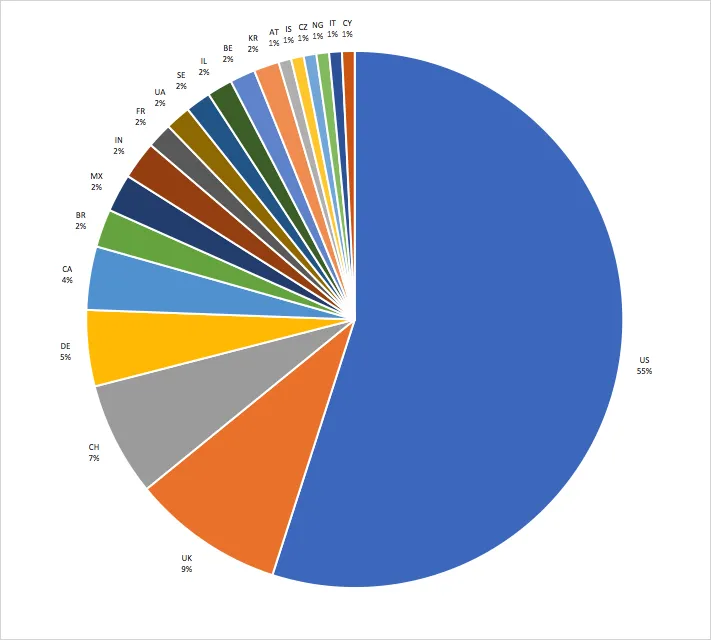
Roughly 2/3 of the targeted organizations are based in the United States, with the remaining targets split between 13 other countries.
The verticals of the targeted organizations fall into several clusters, suggesting that Mercenary.Amanda launched campaigns against specific industries at the order of their clients.
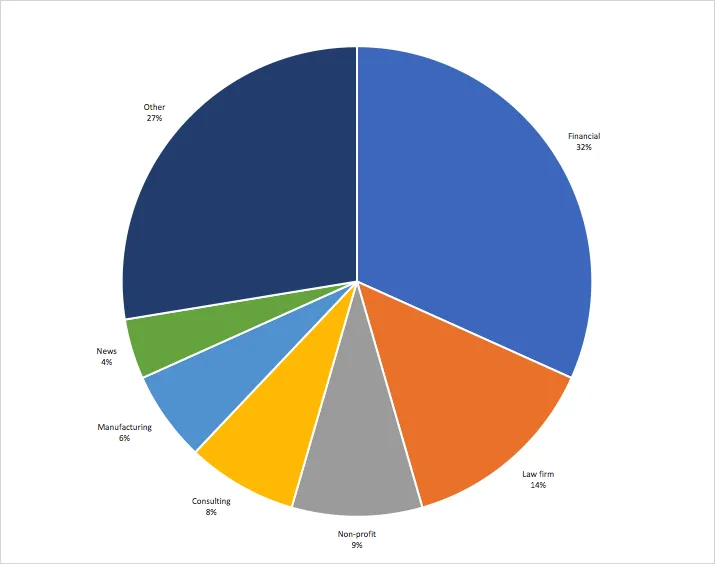
Target Vertical: Financial Services
By far the largest campaign observed from Mercenary.Amanda was targeted at financial services companies. These small and medium-sized businesses all operate in the investment business including fund management, hedge funds, private equity, and financial analysis & advisory.
In the crosshairs were also six financial journalists, both independent as well as employed by global business media outlets. The apparent connection between these journalists were previous publications to investigate accounting irregularities at a German company.
Target Vertical: Law firms
The Mercenary.Amanda target list included a total of 13 renowned law firms in 4 countries: United States, Israel, France, and Switzerland.
Target Vertical: Political Consulting
Another cluster of targets builds around several consulting organizations in the United States that are in the business of public opinion research and political lobbying.
Target Vertical: Politicians
There are multiple clusters in the target list that map to concerted campaigns against politicians and union leaders in at least three countries.
Target Vertical: Non-profit
Another Mercenary.Amanda campaign is aimed at non-profit organizations working on environmental advocacy & climate change policy in the United States and globally. A very detailed description of this campaign is included in the report by Citizen Lab.
Other Targets
There are still dozens of targeted organizations and individuals in the list that do not fall into one of the larger campaigns. This is consistent with the characterization of Mercenary.Amanda as a “hack for hire” actor and would explain the seemingly unconnected target clusters.
Attribution
In the course of the investigation we found several independent trails of evidence that point to an IT company based in India as the entity behind Mercenary.Amanda.
Logging Time Zone
The archives with PHP server code obtained from a Mercenary.Amanda phishing servers include an interesting snippet in the part responsible for logging victim visits.
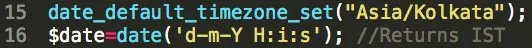
As can be seen the code sets the default time zone for the PHP execution to Indian Standard Time (IST) which is only used in India & Sri Lanka.
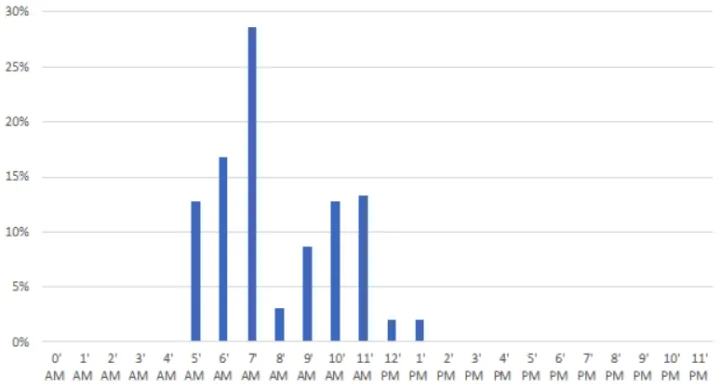
Working Hours
Using telemetry of successfully blocked Mercenary.Amanda phishing emails, we were able to chart the times of day when emails were received. The timing is consistent with a workday in India.
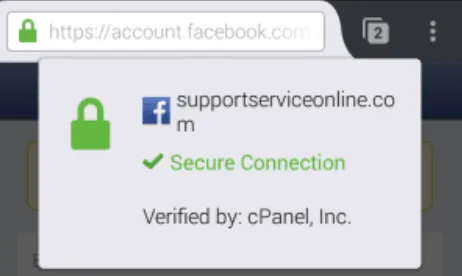
Peerlyst Blog Post
In December 2016, a blog post about using HTTPS certificates in phishing pages was posted on the knowledge sharing platform Peerlyst. The author of the article identified himself as an “Information Security Analyst” at the company that we suspect to be connected with the Mercenary.Amanda phishing campaigns. One of the screenshots in the blog shows a fake Facebook login set up on the domain supportserviceonline[.]com for demonstration purposes.
While searching for indicators for this domain we found URLs submitted to the online security service VirusTotal that used the shortener service pushthisurl[.]com. This shortener domain was used in early 2017 to redirect to the Mercenary.Amanda phishing domain auditionregistrationonline[.]com.
Shortener Leaks
While analyzing the URLs yielded from enumerating shorteners used by Mercenary.Amanda, a number of links were not used to link credential phishing websites. Apparently, the operators used the shortener to exchange URLs including:
- Target research (LinkedIn profiles)
- Links to public cloud storage folders with phishing kits
- Viral videos in Hindi
- Links to products on Indian e-commerce portals
In January 2018, several links appeared on the shortener pointing to listings jobs connected to “offensive security”. This was followed by another public link to cloud storage that included a personal resume apparently stored by one of the operators.
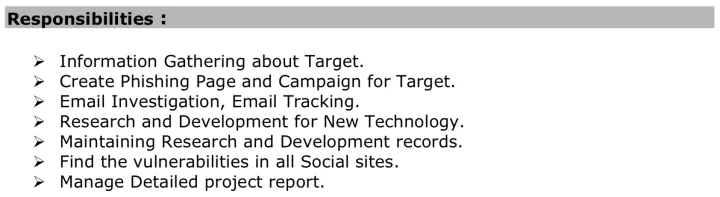
The resume matched an employee of the IT company in the role of “Information Security Analyst” that is linked with high confidence to the campaigns executed by Mercenary.Amanda. The responsibilities listed for their position in the resume distinctively match the phishing operation.







We encourage you to share your thoughts on your favorite social platform.