Tech Support Scammers? Not So Organized Criminals
Technical support scams have been around for years, but they’ve been rapidly increasing in popularity.
Imagine this: You're browsing the internet, and suddenly a website opens, forcing your browser into full-screen mode. It shows a variety of flashy pop-ups and banners, saying “access to your computer has been blocked for security reasons.” The website prompts you to call the support help desk of a well-known technology brand immediately and warns you that your personal information is at risk if you ignore the warnings.
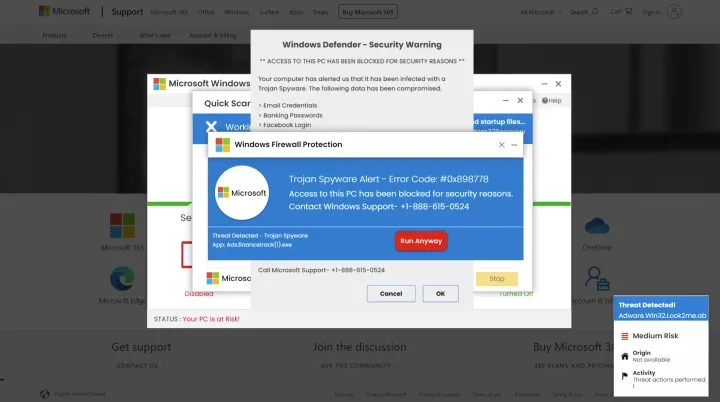
You have come across a “technical support scam,” and it is perfectly safe to simply close the browser. Technical support scams have been around for years, but they’ve been rapidly increasing in popularity, especially on unlicensed streaming sites for movies and sporting events, and other scam sites. These fraudulent companies have grown savvier and adopted more aggressive tactics to lure vulnerable consumers.
The process begins when you visit such a site, where you will be redirected to a different site that hosts the technical support scam. The scam site tries to impersonate real error messages designed to trick you into believing they're genuine software support services on behalf of major technology companies. Most often the error messages contain fake virus warnings or highlight outdated antivirus software. Or they might show a Windows “blue screen of death”, an error screen displayed on Windows following a fatal system error.
Tech support scams don’t necessarily target specific individuals or even actual customers of the brands that they impersonate. They are a global problem potentially affecting everyone. While researching an increase in scams that target the Norton brand, NortonLifeLock Threat Labs also observed tech scams that target customers of Microsoft, Apple, and Amazon.
Scammers often adjust their scam websites to reflect differences in geographic regions to better trick victims into believing they're seeing authentic errors. For example, the next screenshot shows the same page as above, but the language and phone number have been adjusted.
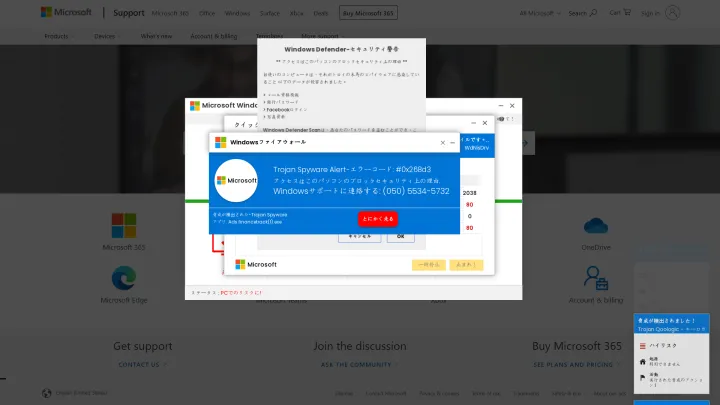
Even though stories of people victimized by scammers are widely covered in the news, the scams continue to be a profitable business model for fraudulent organizations because unsuspecting users continue to fall for them.
Why do we keep falling for them? Unfortunately, there’s no straightforward answer. We respond to emotional triggers, and scammers are trained to exploit these emotions. The stronger the response, the higher the chance the scam is successful. Technical support scams typically exploit fear and urgency as emotional triggers. Fear is the most manipulated emotion, but it often works best when combined with urgency.
The following fake security warning demonstrates the use of fear and urgency well. It falsely warns that if the user does not call Microsoft support immediately, the device will be locked. Additionally, ignoring the warning will put their personal information at risk and will lead to a suspension of the Windows registration.
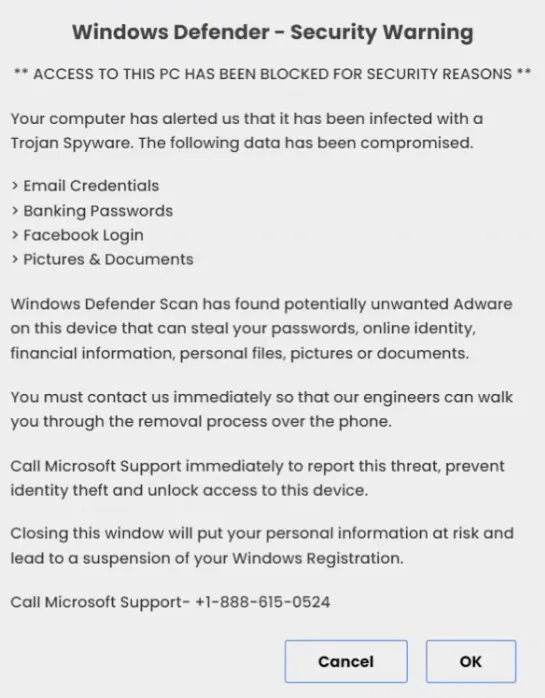
Scammers frequently combine fear and urgency to push you into a state of panic, which in turn drastically increases the chance of successfully tricking you into complying with their scam instructions. Remember, if you come across a website that fills you with dread, it is highly likely that whoever created it wants you to panic. Recognizing these feelings of fear and urgency can serve as a warning that something may not be quite right. Thinking carefully can help you avoid becoming the next victim.
Tech Support Scams using the Norton brand
Browser pop-ups are not the only way for scammers to deceive you. Another method that scammers frequently use is unsolicited cold calls. For example, you would receive a call from someone claiming to be from Norton. The caller will falsely claim your computer is infected with malware or suffering some fictional problems and will then request remote access to fix it. Once the scammer has gained remote access, they may steal your personal information and credentials, install malicious software, or simply upsell their "technical support" for a problem that does not exist.
A common theme for fraudulent Norton tech support scams is “Setup and Activation,” which attempts to trick you into believing you are receiving support from an authorized Norton support and service provider. Many of these scams appear in search engine results, and scammers often use ad services to ensure that their listing is placed first, sometimes before the official Norton website.
Another common method to ensure that websites are listed in search engines is Search Engine Optimization, or SEO for short. Think of a search engine like an answering machine, it goes through billions of websites and indexes, and evaluates the results to determine which content is most likely to answer your query. In simple terms, SEO is there to make sure that the website is responding to the search engine. For example, a website could use the word “Norton Support” and the search engine will know that it should display this website as a result to your query.
Here’s an example of a typical Norton tech support scam. If you typed ‘Norton support’ into a search engine, you could come across a link to a website such as hxxps://2020-norton[.]uk[.]com, which brings up the fraudulent website that is shown in the figure below.

The site has some generic information on how to set up a Norton product and it tries to trick you into believing this is a genuine site by overlaying the actual links with norton.com/setup and misusing Norton logos. Clicking on the "Get Started" button redirects to the next stage of the scam: the download, which in this case is hosted on hxxps://a1norton[.]com.

This second page looks like the first one shown above. It also has generic information and fraudulent logos, but it tries to deceive you into starting the download for the software. Clicking on the "Start Download" button directs to yet another site (hxxps://yelubook[.]com/setup), on which you are asked to provide personal information and, optionally, the Norton product key. This scam is geographically restricted to the United States of America, United Kingdom, Australia, and Canada.
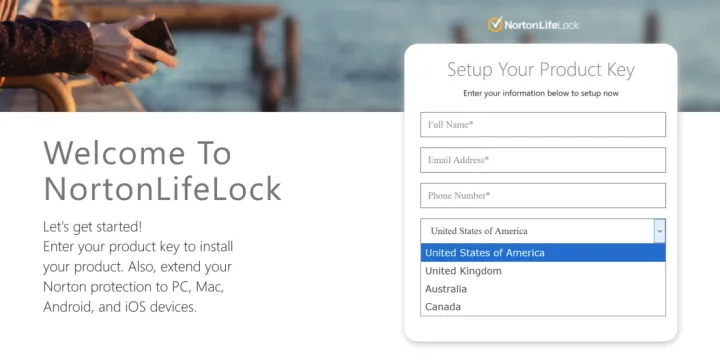
The look and feel of the website changes slightly and you may notice the “We Are Here!” icon in the right bottom corner, which brings up a chat window that allows direct contact the fraudulent “support” team. After providing the required information, the browser is redirected to yet another page designed to tricks you into believing the software is being downloaded.
However, this “download” page is simply a filler page to make this scam more believable before the following error page is shown with fake support phone numbers.
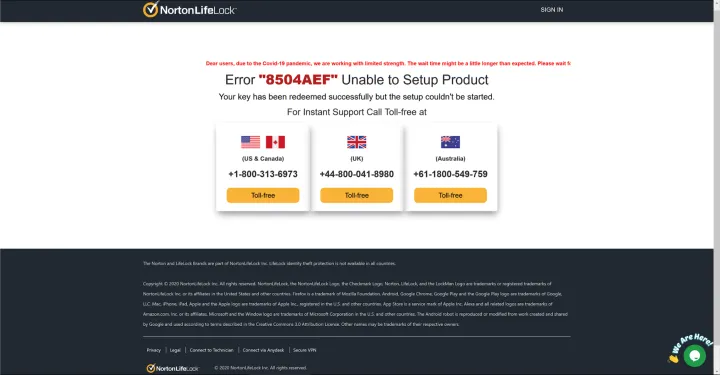
Calling any of the toll-free numbers will connect you to the same call center from which the scammers are operating. The scammer will ask you to install software on your computer that allows them to gain remote access to it. They will then run several benign commands that may look as if they are trying to fix your problem. In our experiment, the scammer quickly determined that the computer was part of a botnet (which it was not), and that the fictional botnet infection contributed to the failure of the download. To fix the computer, the scammer offered to install a "firewall" for $149.99.
The “N0rt0n helpli0ne” support scam campaign
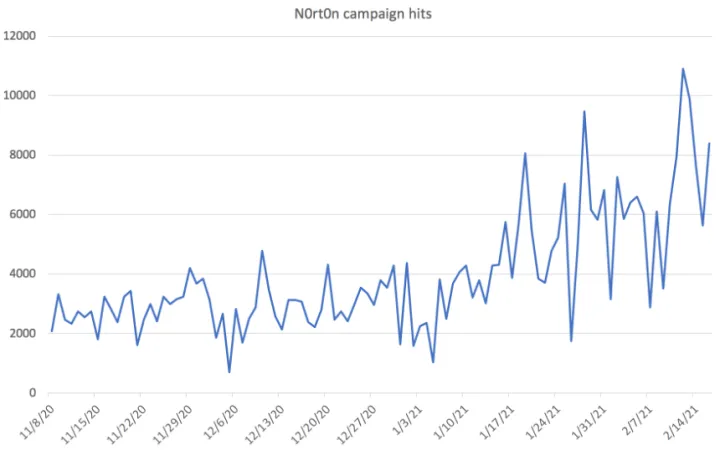
NortonLifeLock Threat Labs researchers have been tracking an extensive support scam campaign targeting the Norton brand that started in early November 2020 and is ongoing. During this time, the scammers registered and used almost six new domains on average per day for a total of 577 domains. These domains were registered with relatively obscure top-level domains .cf (Central African Republic), .ga (Gabon), .gq (Equatorial Guinea), and .ml (Mali). The hosting infrastructure behind the attacks was not visible, however, because the servers were set up to use a content delivery network service offered by Cloudflare.
Similar to other websites described in this article, a user being redirected to this scam site will experience a supposed antivirus scan that always ends in the fictitious detection of the same threats. After the page switches the browser to full-screen mode, several warning messages pop up:
- Your PC is infected with fiver viruses!
- ACTION REQUIRED!
- Your Computer is Infected with TROJAN!
- Threat Detected!
At the same time, a beeping sound is played in a loop while a computerized female voice announces that the “computer has been locked up” and to “call the support number.”
Below is an example URL as used in the scam campaign:
https://gop0her484[.]gq/XN0rt0nDhelpli0nexY1850563/WinY8884sec0urity0119yyY88Y/
While the scam URLs include several random characters and digits, all entries included the terms “N0rt0n” and “helpli0ne,” which prompted us to name this campaign accordingly.
In total, we observed over half a million attempted redirects to URLs used in this support scam campaign in our customer telemetry between Nov. 8, 2020 and Feb. 16, 2021.
Norton Safe Web technology, which scans, categorizes, and provides a reputation score for websites, was able to block 64.2% of attempted redirects to URLs used in this support scam campaign. Norton Safe Web delivers information about websites based on automated analysis and user feedback. We use this research data to improve our detection and to better protect customers.
There are two distinct methods in which scammers attempt to trick you into thinking they’re calling from a legitimate place of business and from a location that is familiar to you. In the first one, scammers are purchasing legitimate phone numbers from VoIP (Voice over Internet Protocol) providers, and sometimes they even purchase toll-free numbers to maintain the guise of a legitimate hotline.
Scammers will purchase phone numbers where the country code matches the geographical location of the intended target. To you, it will appear as if you were dialing a call center within your country when, in fact, the call is routed over VoIP to the scammers’ country and call center. Just because a phone number appears to correlate to where you live (i.e. your country) does not mean the person on the other end of the line is local to you.
The second method scammers use is a bit more sophisticated, but fortunately, it is only used by scammers who cold call you. This method uses spoofing technology, which exploits caller IDs, to make it appear that the caller is coming from a well-known source. This method is commonly used in tax scams, where the scammer spoofs their number so it appears that it is coming from the Internal Revenue Service (IRS), for example. If you see that the call is originating from a trusted source, you are more likely to answer the call than if it was from an unrecognized or unknown number.
Undercover with a Tech Support Scammer
To get a deeper understanding of how these scams work, we decided to call a Norton-impersonating scam support line, armed with a fake persona and a problem that did not exist. We were greeted with an automated message: “All of our representatives are busy helping other customers, your waiting time could be longer than usual. Our working hours are from 9 a.m. to 5 p.m. Eastern Standard Time. If you are calling us out of our business hours, please call us back within our opening hours.”
To our surprise, the scammer picked up the line shortly after we heard the end of the message, greeting us with: “Hello thank you for calling support, how may I help you?” We noticed that the scammer did not mention the company he was providing support for. This is a common technique for scammers because the call centers are often providing scams for a variety of different companies.
We introduced ourselves and informed him that while we were checking our emails, a Norton AntiVirus pop-up appeared on-screen, prompting us to call support. The support agent proceeded with a verification process by asking for personal information, including full name, email address, and date of birth. He pretended to verify my details and said, “OK, see if the Norton came up that moment when you were looking at emails, you might have some security problems [sic].” Without taking a closer look at our issue, he continued, “So in order to fix your problem, we have to, you know. Like, run some security tools for that, to remove all the viruses or something like that. There will be a one-time charge of $150, would that be okay for you?”
We asked whether he thought that our computer had severe problems, knowing that in truth, he knew nothing about the state of our computer, and he only replied with “Yes, so what you need to do is get a prepaid card from the nearest store, Walmart, Walgreen, or 7Eleven, or something like that. Once you have activated the card, call back on the same number and ask for my name, David Parker.” We reluctantly agreed to purchase the prepaid card and that we would call him back in about an hour.
We obtained virtual credit card details and called him back. It took us a few tries to get through to the support line queue, indicating that the hotline was remarkably busy that day and that there wasn’t enough throughput available to be placed in the queue.
After a brief hold in the queue, “David Parker” answered the phone. He seemed quite happy, maybe a little bit surprised, that we called him back, and he asked us whether we managed to get the card, where we purchased the card, and how much money we loaded onto it. We confirmed all details with him and were asked to provide the credit card number, expiration date, and the three-digit security code for a total of three times.
Once he was satisfied that he had written down the correct details, David prompted us to open a link to a remote support tool that would allow him to log on to our computer. He explained the steps to us that would grant him full remote access to our computer, a specially created virtual machine. This level of access would have allowed him to copy files, install and remove software, and even reboot the machine.
David’s level of technical expertise became apparent once he logged onto the computer. He opened the command line terminal and ran “tree,” a basic command that simply cycles through the directories on the hard drive and displays the results in the terminal window. To a non-technical person, this command may look like the scammer is troubleshooting our system, when, in fact, it contributes nothing to solving the “issue” we have been having.
David continued to open Windows Event Viewer, a built-in tool that allows users to view logs, and filtered for warning messages, to tell us that we have approximately 1,000 viruses on the computer. Again, to a non-technical person, the warning messages could indicate that something is incredibly wrong with the machine when, in fact, the warning messages are quite a normal thing to see in Event Viewer.
We were placed on hold for around 20 minutes while the scammer was looking through the contents of the computer. He did not perform any additional troubleshooting steps and told us that he would be transferring this call to a level-five technician. The level-five support agent spent another 20 minutes looking through the computer to make it look like he was doing work, while simultaneously combing through the file system, probably looking for any sensitive information to copy and exfiltrate using the backend of the remote client.
If it isn’t clear by now, these scammers wasted nearly an hour of our time pretending to fix an issue that didn’t exist while charging us $150 for the privilege. Had any files with personal information existed within our research virtual machine, there’s a possibility that these scammers could have stolen them and used them for some other nefarious purpose.
How to identify tech support scammers:
- Make sure to check the web address you are visiting. For Official Norton Support, confirm that the website address displayed is https://support.norton.com.
- You should never make a payment over the phone unless it is a call that you have initiated, and you have verified the number that you are calling is legitimate. Use official contact details from the company website.
- Never hand money over to someone who has called you unexpectedly. Companies like NortonLifeLock, banks, utilities providers, and governments will never cold call customer and ask for personal information, bank details, or gift card payments.
- You will NEVER receive an unsolicited call from Official Norton Support to fix issues with your computer for money (You will only receive a call if you request it.)
- Official Norton Support comes with your subscription at no additional cost. Our support teams will never ask that you pay for support in the form of gift cards or Bitcoin.
- If your computer displays pop-ups and error messages with a phone number, don’t call the number. For Norton subscribers, keep in mind that when the software detects a threat, it will never ask you to call Official Norton Support via a toll-free number.
Be wary of letting an unknown company or support agent gain remote control over your computer or conduct a remote session on your device. Keep your computer and other devices up to date with the latest version of reputable security software with malware protection.
What we are doing to protect customers
Tech support scams are a scourge on the internet, relying on fear to trick innocent people into spending their hard-earned money on services they don’t need. Detecting and disrupting these tech support scams takes time and continuous effort. Like many social engineering attacks, customer awareness and education are critical defenses. To help protect and educate NortonLifeLock customers, we publish blogs, support articles and resources, and videos on tech support scams.
We are also committed to tackling the issue head-on through new research initiatives. Scammers’ activities leave behind clues that we monitor such as domain names that deceptively mimic our brand. Additionally, we are developing machine learning techniques to filter through suspected scam pages. We expect to continue these research efforts and continue working with authorities to identify and enforce against infrastructure that harms our customers and infringes our intellectual property.
We empathize with our customers and are dedicating research and development efforts to educate and help protect our customers from these scams.
What You Can Do If You Have Been Scammed
If you feel you have been misled and/or have been unfairly charged money by another company we recommend the following actions:
- Change your passwords: to your computer, to financial institutions, to your Norton Account and any other password protected websites that you visit. If you’re an existing Norton customer, log into your Norton Account at my.norton.com.
- Run a Full System Scan for viruses on your computer.
- Contact the company that charged you and request a refund.
- If you cannot get a refund directly from the company, contact your bank to report the problem.
- File a complaint with appropriate authority: Competition & Consumer Protection Authorities Worldwide
Competition & Consumer Protection Authorities Worldwide.
How To Get Official Norton Support?
- Official Norton Support is FREE to current subscribers.
- The Official Norton Support webpage is located at https://support.norton.com.
- You will NEVER receive an unsolicited call from Official Norton Support to fix issues with your computer for money (You will only receive a call if you request it.)
For more information, please read:
- NortonLifeLock Tech Support Scam Information
- Fraudulent Uses of the NortonLifeLock Brand
- How to recognize and avoid tech support scams | Norton
Indicators of Compromise
| Domain | Language(s) | Phone number |
|---|---|---|
| errorinthepc[.]xyz | English | + 1-888-373-3953 |
| microsoftinvoice[.]tech | English | + 1-800-861-914 |
| 01-norton[.]xyz | English | + 1-562-367-3494 |
| callsupportforassisstance80[.]gq | English | + 1-833-220-3560 |
| recerror[.]xyz | English | + 1-888-373-3953 |
| suppor-err-tracking59446[.]tk | English | + 1-800-916-4210 |
| warrenty-alertm[.]xyz | English | + 1-888-501-301 |
| amazingsecure[.]xyz | English | + 1-888-571-289 |
| clean-pc-now[.]xyz | English | |
| fr-win-scan24[.]xyz | French | + 33-0-185-155-919 |
| fr-windows-admin[.]xyz | French | + 33-0-185-155-919 |
| wingrowth[.]online | Japanese | + 81-50-5539-8251 |
| mail-queue27[.]fun | Japanese | + 81-50-5809-3209 |
| alertfix[.]site | Japanese | + 81-50-5534-4005 |
| esafeworld[.]xyz | Japanese | + 81-50-5534-5732 |
| ichichi[.]xyz | German | + 41-800-110-328 |
| pack-on-hold[.]com | English/Portuguese/Spanish | |
| protect-your-pc[.]xyz | English/Portuguese/Spanish |
Editorial note: Our articles provide educational information for you. NortonLifeLock offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about cyber safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses.
Copyright © 2021 NortonLifeLock Inc. All rights reserved. NortonLifeLock, the NortonLifeLock Logo, the Checkmark Logo, Norton, LifeLock, and the LockMan Logo are trademarks or registered trademarks of NortonLifeLock Inc. or its affiliates in the United States and other countries. Other names may be trademarks of their respective owners.













We encourage you to share your thoughts on your favorite social platform.