Consumer Cyber Safety Pulse Report – From Norton Labs


Your Cyber Safety is linked to COVID-19 global trends. Pandemic-related scams and threats targeted consumers in the first three months of 2021. The outlook? Expect similar threats ahead tied to reopening activities.
That’s according to Norton Labs, the team behind Norton products that monitors online threats to help keep you Cyber Safe. Learn more here, in our first Consumer Cyber Safety Pulse Report, published quarterly.
Fast fact: Phishing campaigns are the No. 1 threat to Cyber Safety. Most privacy and security scams begin with a phishing email designed to trick you into compromising your privacy and security and steal your money. Scammers often send urgent messages that prey on consumers’ fears and concerns of the moment — meaning, phishing scams will be with us for a long time.
What happened: Here’s what the Norton Labs team detected in the first quarter of 2021.
- Vaccine-oriented scams.
- Tax refund and financial relief scams.
- Tech support scams.
What’s ahead: In the next three months, expect fraudsters to focus on a gradual shift to a post-COVID state. That means more people working on site, traveling, and engaging in social activities.
Here are three things to watch out for:
- Vaccine passport fraud.
- Ransomware attacks.
- Supply-chain attacks.
The look back: Consumer Cyber Safety threats by the numbers
NortonLifeLock technology blocks more than 9 million threats on average every day. Here’s a closer look at the numbers over the past 100 days, according to the Norton Labs team.

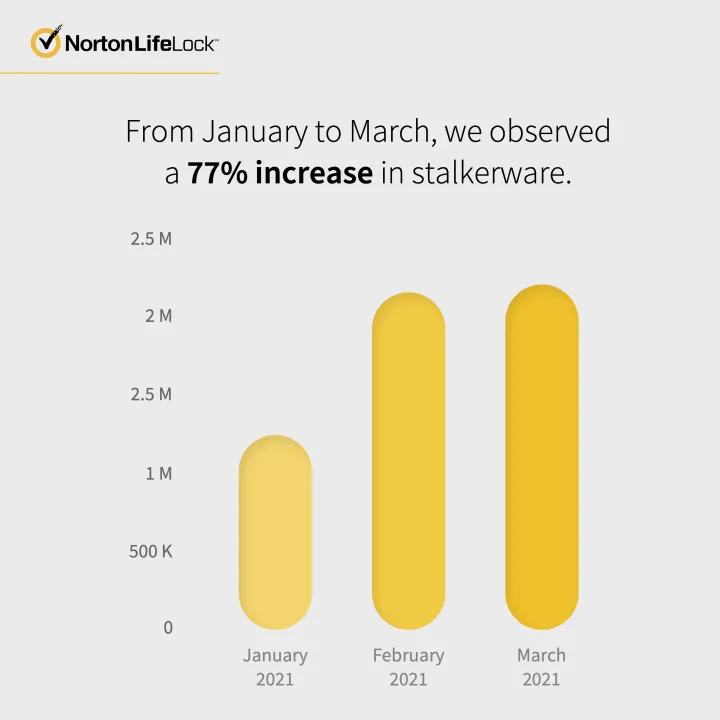
Cyber Safety spotlight: Stalkerware detections rising
Stalkerware — also known as spyware — is a type of malware designed to secretly monitor your activity on your smartphone, laptop, or tablet, sometimes with dangerous intent. For instance, abusers might use stalkerware to spy on an ex-spouse. The Norton Labs team detected a surge in emails purporting to sell stalkerware and blocked those attempts.
Scam roundup: 5 scams you should know about and how they work
The Norton Labs team gathers more than data. It also highlights examples of phishing emails and other information to show consumers how scams and security threats work.
Here are five examples that can help you stay Cyber Safe.
- Cryptocurrency and crime. Future money or ransomware vehicle?
- Phishing and smishing. Scams can land in your inbox or on your phone.
- Tax fraud. Your personal information can be used to steal your refund.
- COVID 19 vaccination scams. You want health, they want money.
- Gaming threats. Your gaming account could be worth a lot. Scammers know this.
1. Cryptocurrency and crime
As cryptocurrencies become more popular, so do crimes associated with them.
Background: Cryptocurrency is a form of payment that can be exchanged online for goods and services. Cryptocurrencies work using a technology called blockchain. Blockchain is a decentralized technology spread across many computers that manages and records transactions. Part of the appeal of this technology? Its anonymity.
Cybercriminals engage in two activities to obtain cryptocurrency: illicit coinmining and ransomware.
1. Illicit coinmining — and what it could mean for your electric bill
Criminals hijack consumers’ systems to obtain cryptocurrency through coinmining. If your computer is infected, your electric bill could reflect this energy-intense practice.
Coinmining never really went away, but it has come roaring back. Over the course of 12 months the price of Bitcoin quadrupled, and that attracted criminals looking to make an easy buck by stealing your computer's horsepower.
Unlike ransomware, coinminer malware stays in the background so that it can stealthily mine cryptocurrency. It does this by using resources from an infected computer or smartphone such as the processor, graphics card, memory, and network bandwidth.
Malware authors are taking advantage of the price trend and increasingly spreading malware that aims to exploit other people's computer resources for illegal mining activities.
2. Ransomware: Where your locked data and crypto meet
Thanks in part to crypto’s anonymity, cybercriminals operating ransomware campaigns require payment in cryptocurrency. This led to a rise in ransomware in recent years, including a 35% jump in ransomware attacks from late 2020 to early 2021.
How it works: Consumers have easy access to cryptocurrencies through services like Coinbase, Robinhood, and PayPal. That means criminals have an anonymous, reliable payment method to monetize crime. Bottom line: Criminals don't care what you're doing, they just want their money.
The outlook: Cryptocurrencies are not going away. This indicates the threats of ransomware and illicit coin-mining will continue to grow, short of real digital currency overhaul and regulation.
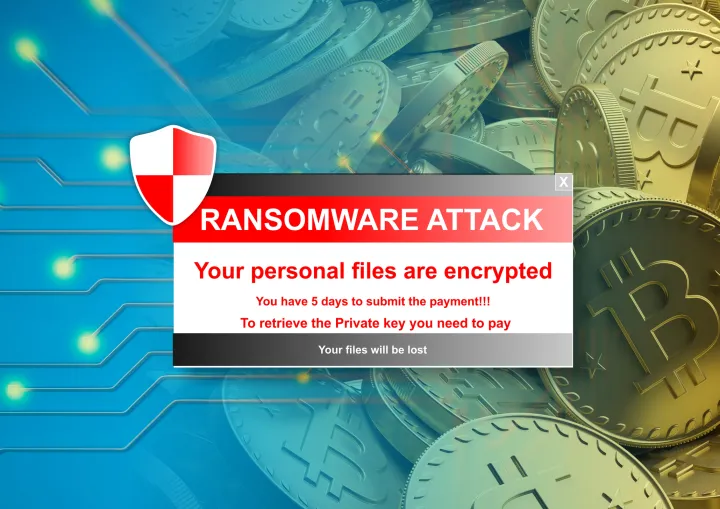
Consumer impact: Consumers pay ransomware gangs in cryptocurrency to get their data back and for the promise their stolen data won’t be leaked to the public.
The new twist: Rather than just lock/delete the consumer data, we’ll see the double threat of locked data and — if that threat doesn’t work — a release/leak of sensitive personal data such as sensitive selfies, private conversations, and other things people would rather keep secret, as well as reputation attacks. Double threat, double trouble. Consumers may also see slower device performance and higher energy bills due to illicit and unwanted coin-mining.
2. Royal mail phishing – smishing
Scams often arrive not only by email, but also by text message.
How it works: The BBC published an article on March 23 about the Royal Mail phishing campaign. A young woman, a drama student, fell victim to the text message scam that is highlighted below.
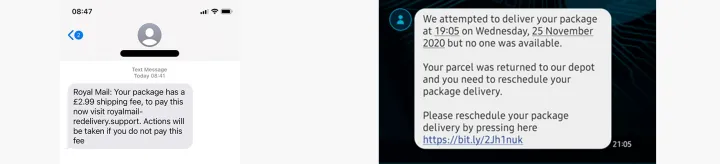
Her birthday was coming up, and she was in a hurry. She thought nothing of the message and entered her bank details.
The next day, a man pretending to be from Barclays, called her and told her that someone had tried to set up direct debits in her account. The scammer told her she needed a new bank account because entering her details online put her at risk. He persuaded her to transfer all her savings into a new account.
Since this story was shared, hundreds of other people joined in sharing their own stories of similar scams.
Learn more: https://www.nortonlifelock.com/blogs/research-group/flubot-targets-android-phone-users
3. Tax fraud and phishing
How it works: Attackers attempt to defraud tax payment and refund systems. Often, this means impersonating the IRS or official government sites in phishing setups. Phishing campaigns against these targets do not appear to strictly follow tax seasons, but instead come in campaign waves.
Here’s an example from January of a convincing IRS phishing page.
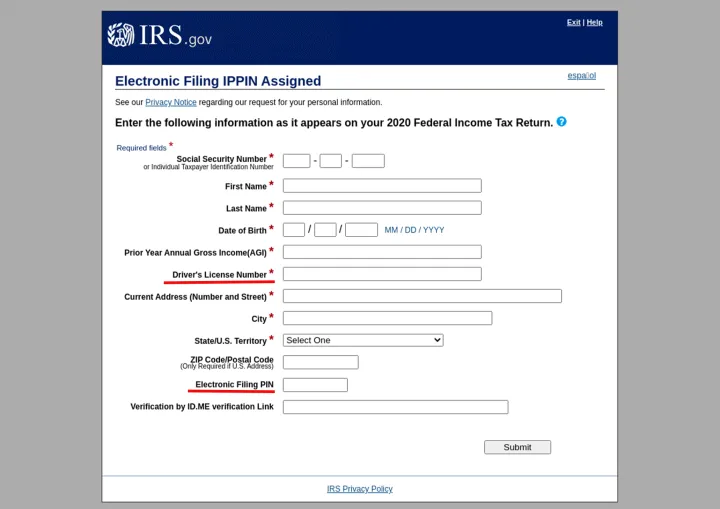
Learn more: To find out what tax-related scams look like and how to avoid them, this article from the Labs team can help.
4. COVID-19 vaccination scams
Scams associated with the COVID-19 have thematically followed the phases of the pandemic — COVID alerts, personal protection equipment scams, virus test and tracking phishes, stay-at-home giveaway lures, and refund and relief fraud.
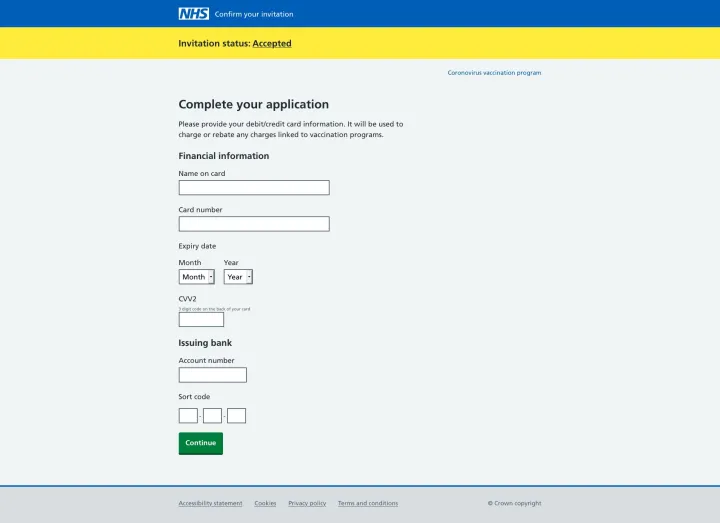
Following the development of COVID-19 vaccines, a wave of vaccine scams preyed on people’s desire to get vaccinated. In April 2021, the UK National Health Service was the target of a vaccination-themed campaign, as shown below.
How it works: After providing personal information, victims are required to enter financial information. The phishing page actively checks for valid credit card numbers and fails if an incorrect number is entered. The gathered data is sent off to the attacker's server before the user is redirected to the genuine NHS site.
5. Threats in gaming
Gamers are attractive targets for attackers. Game accounts are valuable and can be sold in underground forums for cash. Same with in-game items and currency.
Regular phishing campaigns to access game accounts are common.
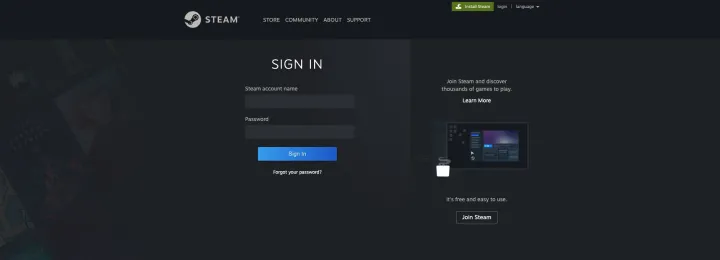
How it works: Here’s a fake Steam login designed to steal login credentials.
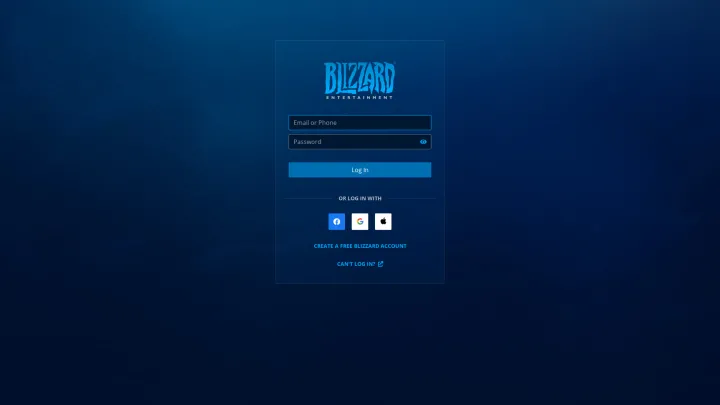
Another example is the Blizzard accounts phish.
Blizzard account thefts usually start with an in-game message in World of Warcraft. The threat actor poses as a Blizzard Game Master, telling the victim that their account violated terms and conditions and then prompts the user to visit a website to avoid permanent suspension of the account.
The link leads the victim to a convincing phishing site that looks similar to the legitimate one. After entering the login credentials, the victim gets redirected to a second page where they have to enter a verification code that was sent by email from a genuine Blizzard address.
After providing the code, the victim then gets redirected to the final page where they must select a security question and provide the corresponding answer. The website then highlights a message that the victim successfully passes verification before redirecting them to the genuine Blizzard website.
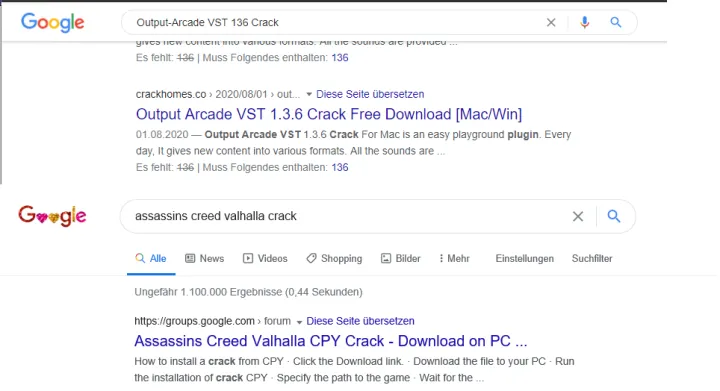
Another threat targeting gamers? The “Trojanized” crack campaign. A crack is a way to bypass software licensing.
How it works: Trojanized cracks are being distributed from sites that show up very early in Google searches. The crack installs a variety of highly malicious software.
Sites tell users to manually disable antivirus protection before they install, and Norton Labs sees that users listen: Telemetry shows that we mainly see the malware during support cleanup, not initial infection as the user had disabled the antivirus protection.
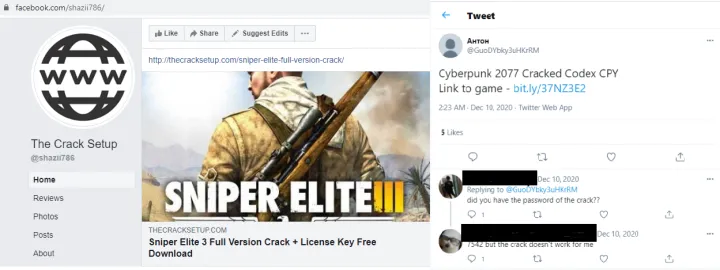
You can see how the crack campaign also abuses regular software vendors, like Norton.
Looking ahead
The Norton Labs continues to track scams and threats targeting consumers. Expect the pandemic-theme to continue, but other world events will likely have an impact.
Find out more when we publish our next Consumer Cyber Safety Pulse Report in August.
Innovations from Norton Labs are for research, evaluation, and consumer feedback purposes. NortonLifeLock does not give any warranties as to the suitability or usability of these prototypes and recommends safeguarding data and reviewing all terms and conditions before use.
Copyright © 2021 NortonLifeLock Inc. All rights reserved. NortonLifeLock, the NortonLifeLock Logo, the Checkmark Logo, Norton, LifeLock, and the LockMan Logo are trademarks or registered trademarks of NortonLifeLock Inc. or its affiliates in the United States and other countries.