Threat Actors Cash in on COVID related Tax Refund Scams
Watch out for these attempts to get your money and personal identifying information
NortonLifeLock Labs continues to observe threat actors targeting COVID-19 tax-relief schemes offered by governments across the world.
Most notably, we have seen the UK’s Her Majesty’s Revenue and Customs (HMRC) and the USA’s Internal Revenue Service (IRS) tax bodies being spoofed. Threat actors lure the victims with crudely crafted phishing emails that inform recipients that they are entitled to a considerable tax rebate or financial support during the pandemic.
People around the world are feeling the economic strain caused by global lockdowns, mass redundancies, and reduced working hours. Threat actors know this. They attempt to exploit people’s hardship by offering the lure of a tax rebate.
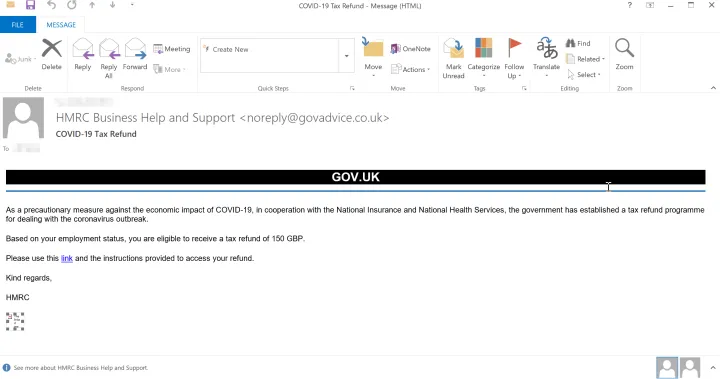
In the HMRC scam, the email body informs the victim that they are eligible for a tax refund program to help alleviate some of the financial strain caused by the pandemic. It contains an embedded hyperlink that redirects the unsuspecting victim to a phishing page, which intends to harvest a wealth of personal information.
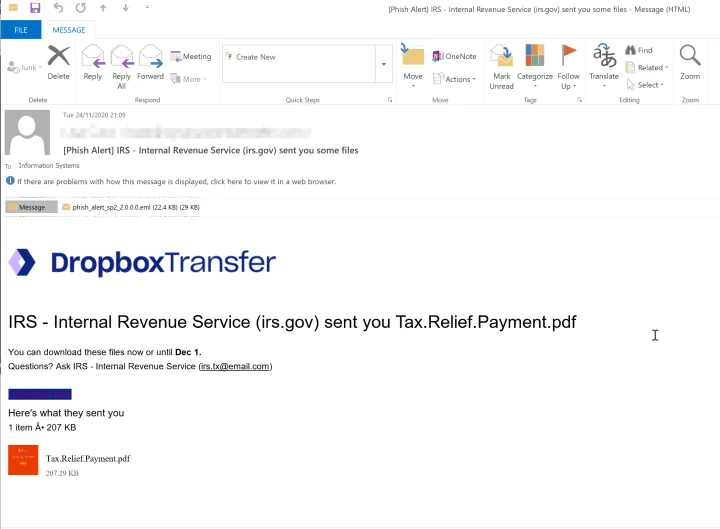
The IRS phishing email is a little more sophisticated in terms of attempting to bypass security filters and antivirus technologies. The example above uses an embedded hyperlink, which redirects the user to Dropbox where a PDF file is hosted. The PDF file then contains another embedded link, which redirects the user to a phishing page.
Dropbox is typically defined as a trusted business application, and a PDF is a trusted file type in most organizations. Using these sources to deliver a malicious URL to the end user can help bypass content filtering and URL scanning of most secure email gateways.
Phishing pages
Threat actors target different types of personal information. Some harvest user names, email addresses, and passwords, while others — as in the IRS phishing campaign — target Social Security numbers and photo ID information.
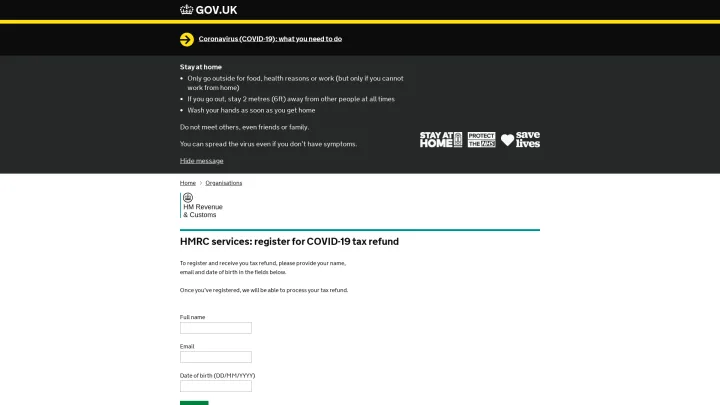
Armed with this wealth of personal information, a determined threat actor can completely hijack a person’s identity to open bank accounts and apply for credit in the name of the victim. These personal details are also usually sold on premium crimeware forums on the dark web for the purpose of money laundering and other criminal activities.
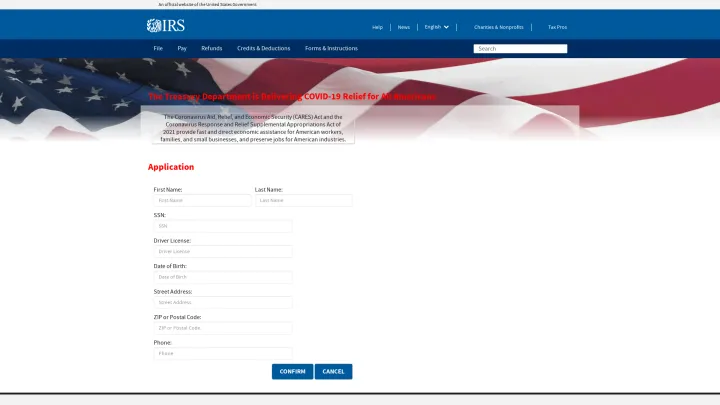
Examples of the IRS tax refund scams aim to harvest a comprehensive list of personal information as you can see in the example above. In Fig. 4, the malicious actors ask for the full name and address of the victim, their Social Security number, and driver’s license number. It also requests the user upload a photocopy of the front and back of an ID card.
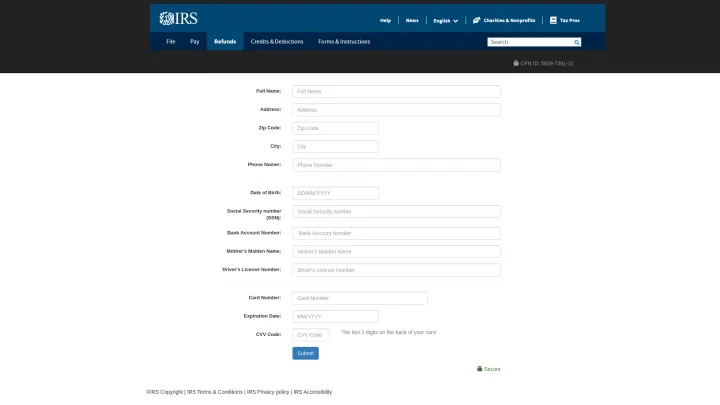
We also observed a variant of the attack specifically targeting credit card information. As you can see below, the phishing pages were set up to harvest the card number, expiration date and three-digit security code on the back of the card. The victim is asked to confirm their credit card details before a tax rebate is supposed to be paid out. This should be a major red flag because a consumer should never have to confirm such details to receive a government payment of any kind.
Remediation
Most tax authorities will not contact you and ask you for your bank details, PIN, or passwords. Never give out private information over the phone, reply to text messages, download attachments, or click on links that you were not expecting. Always verify with your local authority that the communication you received is genuine. Most tax authorities will have a hotline that you can contact if you suspect you have been targeted by scammers. Contact your bank immediately if you suspect you have submitted your bank details to a phishing page.
How to report scams to HMRC:
- Take action – forward suspicious emails claiming to be from HMRC to phishing@hmrc.gov.uk and texts to 60599.
- Check GOV.UK for information on how to avoid and report scams.
How to report scams to IRS:
-
Don't click on any links. Visit the IRS identity protection page if you clicked on links in a suspicious email or website and entered confidential information.
-
Forward – preferably with the full email headers – the email as-is to the IRS at phishing@irs.gov.
Indicators of Compromise
IRS URLs
- hXXp://covid-stimulus[.]org/
- hXXp://disvey[.]ir/authcovid-19reliefgov/?labor_department
- hXXps://routerbotic[.]com/irs-corona-payment-monthly/
- hXXps://snreklame[.]com/mobile-authcovid-19gov/?labor_department
- hXXps://irsfgov[.]com/
HMRC URLs
- hXXp://mail[.]lockdown-support[.]org/refund/index?code=2
- hXXps://gov[.]pandemic-recovery[.]org/covid-19/Login[.]php?
- hXXps://govuk-alerts[.]net/refund/index?code=2
- hXXps://govlockdown[.]org/refund/index?code=2
- hXXps://govlockdown[.]com/refund/index?code=2







We encourage you to share your thoughts on your favorite social platform.